Security News

As the Ring Android app has over 10 million downloads and is used by people worldwide, the ability to access a customer's saved camera recordings could have allowed a wide range of malicious behavior, ranging from extortion to data theft. When analyzing the Ring Android app, Checkmarx found that the app was exposing an 'activity' that could be launched by any other app installed on the Android device.

In a sign that malicious actors continue to find ways to work around Google Play Store security protections, researchers have spotted a previously undocumented Android dropper trojan that's currently in development. Dubbed BugDrop by the Dutch security firm, the dropper app is explicitly designed to defeat new features introduced in the upcoming version of Android that aim to make it difficult for malware to request Accessibility Services privileges from victims.

Roid malware developers are already adjusting their tactics to bypass a new 'Restricted setting' security feature introduced by Google in the newly released Android 13. Roid 13 was released this week, with the new operating system being rolled out to Google Pixel devices and the source code published on AOSP. As part of this release, Google attempted to cripple mobile malware that attempted to enable powerful Android permissions, such as AccessibilityService, to perform malicious, stealthy behavior in the background.
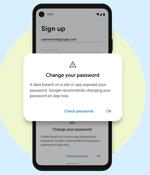
Google released Android 13, and it is already rolling out to eligible Pixel smartphones. In this Help Net Security video, you'll learn more about the latest privacy and security features of Google's mobile operating system.
The SOVA Android banking trojan is continuing to be actively developed with upgraded capabilities to target no less than 200 mobile applications, including banking apps and crypto exchanges and wallets, up from 90 apps when it started out. In less than a year, the trojan has also acted as a foundation for another Android malware called MaliBot that's designed to target online banking and cryptocurrency wallet customers in Spain and Italy.

The Australian Competition and Consumer Commission announced that Google was fined $60 million for misleading Australian Android users regarding the collection and use of their location data for almost two years, between January 2017 and December 2018. "Google, one of the world's largest companies, was able to keep the location data collected through the 'Web & App Activity' setting and that retained data could be used by Google to target ads to some consumers, even if those consumers had the"Location History" setting turned off," said ACCC Chair Gina Cass-Gottlieb.

The SOVA Android banking trojan continues to evolve with new features, code improvements, and the addition of a new ransomware feature that encrypts files on mobile devices. With the latest release, the SOVA malware now targets over 200 banking, cryptocurrency exchange, and digital wallet applications, attempting to steal sensitive user data and cookies from them.

Eighty-five percent of users are most interested in finding out how to set up privacy settings for services on Android, according to data collected by Kaspersky's Privacy Checker website. Concerns over digital privacy are widespread. A "Digital Privacy and Security Survey" conducted by the Calyx Institute in 2021, found that 80% of respondents were worried about the topic of digital privacy over the last year and 59% said they felt more aware of how their data is treated than a year ago.

Meta first reported the new Android malware in its Q2 2022 adversarial threat report, where they briefly mentioned its data-stealing, geo-locating, and microphone-activation capabilities. While Meta mentions laced versions of Telegram, WhatsApp, and YouTube, Cyble's investigation only uncovered a trojanized version of the Signal messaging app.

Meta has released its Q2 2022 adversarial threat report, and among the highlights is the discovery of two cyber-espionage clusters connected to hacker groups known as 'Bitter APT' and APT36 using new Android malware. These cyberspying operatives use social media platforms like Facebook to collect intelligence or to befriend victims using fake personas and then drag them to external platforms to download malware.