Security News

Twilio has denied in a statement for BleepingComputer that it was breached after a threat actor claimed to be holding over 89 million Steam user records with one-time access codes. [...]

Coinbase has fixed a confusing bug in its account activity logs that caused users to think their credentials were compromised. [...]

Coinbase is fixing an incorrect account activity message that freaks out customers and makes them think their credentials were compromised. [...]

Who knew social media stars had a role to play in building national cyber resilience? The world's biggest brands have benefited from influencer marketing for years – now the UK's National Cyber...

Cybersecurity researchers have detailed a new adversary-in-the-middle (AitM) phishing kit that's capable of Microsoft 365 accounts with an aim to steal credentials and two-factor authentication...
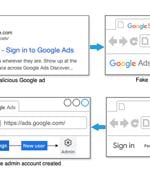
Cybersecurity researchers have alerted to a new malvertising campaign that's targeting individuals and businesses advertising via Google Ads by attempting to phish for their credentials via...

A new phishing-as-a-service (PhaaS) platform named 'Rockstar 2FA' has emerged, facilitating large-scale adversary-in-the-middle (AiTM) attacks to steal Microsoft 365 credentials. [...]

Cybersecurity researchers are warning about malicious email campaigns leveraging a phishing-as-a-service (PhaaS) toolkit called Rockstar 2FA with an aim to steal Microsoft 365 account credentials....

An emerging phishing-as-a-service (PhaaS) platform called Mamba 2FA has been observed targeting Microsoft 365 accounts in AiTM attacks using well-crafted login pages. [...]

Bank customers in the Central Asia region have been targeted by a new strain of Android malware codenamed Ajina.Banker since at least November 2024 with the goal of harvesting financial...