Security News > 2024 > February

Members of the Five Eyes intelligence alliance warned today that APT29 Russian Foreign Intelligence Service hackers are now switching to attacks targeting their victims' cloud services. The Russian cyberspies also compromised Microsoft 365 accounts belonging to various entities within NATO nations to obtain foreign policy-related data and targeted governments, embassies, and senior officials throughout Europe associated in a string of phishing attacks.

Steel giant ThyssenKrupp confirms that hackers breached systems in its Automotive division last week, forcing them to shut down IT systems as part of its response and containment effort. ThyssenKrupp AG is one of the world's largest steel producers, employing over 100,000 personnel and having an annual revenue of over $44.4 billion.

Supply chain attacks are often used, as those attacks allow a threat actor to hit multiple targets easily. No matter the motivation for a cybersecurity attack, identity-based and social engineering attacks are still taking center stage.

This adds up to mean that while cybersecurity training is valuable in building awareness and knowledge about password security, it has limitations in changing risky user behavior like password reuse. By combining training efforts with technology, organizations can create a more robust defense against risky password behavior.
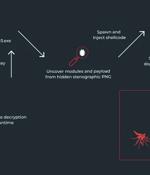
Ukrainian entities based in Finland have been targeted as part of a malicious campaign distributing a commercial remote access trojan known as Remcos RAT using a malware loader called IDAT Loader....

Webinar The original European Union Network and Information Security Directive certainly led to an improvement in member states' cybersecurity defences, but it struggled to do everything required as cyberattacks and threats scaled up with the growth in digitalization. The new legislation expands the NIS security requirements, the scope of covered organizations and sectors.
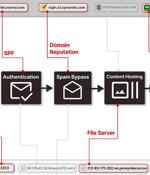
More than 8,000 domains and 13,000 subdomains belonging to legitimate brands and institutions have been hijacked as part of a sophisticated distribution architecture for spam proliferation and...

LockBitSupp, the individual running the LockBit ransomware-as-a-service operation, has made good on one promise: the LockBit leak site is back online on backup domains, with lists of victims expected to be unveiled in the coming days. Last week, Operation Cronos hit LockBit hard by taking over their leak site and affiliate panel, disrupting part of their infrastructure, and arresting some suspected affiliates.

A massive ad fraud campaign named "SubdoMailing" is using over 8,000 legitimate internet domains and 13,000 subdomains to send up to five million emails per day to generate revenue through scams and malvertising. "The campaign is called"SubdoMailing, as the threat actors hijack abandoned subdomains and domains belonging to well-known companies to send their malicious emails.

A massive ad fraud campaign named "SubdoMailing" is using over 8,000 legitimate internet domains and 13,000 subdomains to send up to five million emails per day to generate revenue through scams and malvertising. "The campaign is called"SubdoMailing, as the threat actors hijack abandoned subdomains and domains belonging to well-known companies to send their malicious emails.