Security News > 2023

A pro-Hamas threat actor known as Gaza Cyber Gang is targeting Palestinian entities using an updated version of a backdoor dubbed Pierogi. The findings come from SentinelOne, which has given the...

Russian state-sponsored hackers have been exploiting CVE-2023-42793 to target unpatched, internet-facing JetBrains TeamCity servers since September 2023, US, UK and Polish cybersecurity and law enforcement authorities have warned. As they noted, this time around, "The victim types do not fit into any sort of pattern or trend, aside from having an unpatched, Internet-reachable JetBrains TeamCity server."
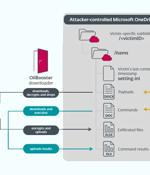
The Iranian state-sponsored threat actor known as OilRig deployed three different downloader malware throughout 2022 to maintain persistent access to victim organizations located in Israel. The...

Network penetration testing plays a crucial role in protecting businesses in the ever-evolving world of cybersecurity. Yet, business leaders and IT pros have misconceptions about this process,...

Network penetration testing plays a crucial role in protecting businesses in the ever-evolving world of cybersecurity. Yet, business leaders and IT pros have misconceptions about this process,...

OAuth is an especially appealing target for criminals in cases where compromised accounts don't have strong authentication in place, and user permissions allow them to create or modify OAuth applications. Microsoft, in a threat intel report, details one cyber crime crew it tracks as Storm-1283 that used a compromised account to create an OAuth application and deploy VMs for crypto mining, while also racking up between $10,000 and $1.5 million in Azure compute fees.

Threat actors affiliated with the Russian Foreign Intelligence Service (SVR) have targeted unpatched JetBrains TeamCity servers in widespread attacks since September 2023. The activity has been...

Attackers are trying to leverage public proof-of-exploit exploit code for CVE-2023-50164, the recently patched path traversal vulnerability in Apache Struts 2. "Attackers aim to deploy webshells, with some cases targeting the parameter 'fileFileName' - a deviation from the original exploit PoC," Akamai's Security Intelligence Group flagged on Wednesday.

Karakurt, a particularly nasty extortion gang that uses "Extensive harassment" to pressure victims into handing over millions of dollars in ransom payments after compromising their IT infrastructure, pose a "Significant challenge" for network defenders, we're told. So to help organizations avoid getting caught by this crew, the FBI, and the US government's Cybersecurity and Infrastructure Security Agency, Treasury Department, and Financial Crimes Enforcement Network released an extensive list of vulnerabilities and methods the gang exploits and uses for initial access, the software tools they abuse to snoop around and steal data, and the payment wallets and even email addresses used in the group's extortion attacks.

Microsoft disrupted an alleged threat actor group that built viable cybercrime-as-a-service businesses. Dubbed Storm-1152 by Microsoft, the group bilked enterprises and consumers globally out of millions of dollars.