Security News > 2023 > August

A previously undocumented threat cluster has been linked to a software supply chain attack targeting organizations primarily located in Hong Kong and other regions in Asia. The attacks, per the cybersecurity firm, leverage a trojanized version of a legitimate software called EsafeNet Cobra DocGuard Client to deliver a known backdoor called PlugX on victim networks.

A previously unidentified APT hacking group named 'Carderbee' was observed attacking organizations in Hong Kong and other regions in Asia, using legitimate software to infect targets' computers with the PlugX malware. Symantec reports that the legitimate software used in the supply chain attack is Cobra DocGuard, created by Chinese developer' EsafeNet,' and used in security applications for data encryption/decryption.

Japanese watchmaker Seiko has been added to ALPHV ransomware group's victim list, following a data breach occurring in early August. The company published a data breach and response notice on August 10, 2023, stating that an unidentified party gained unauthorized access to at least one of their servers.

Juniper Networks has fixed four vulnerabilities in Junos OS that, if chained together, could allow attackers to achieve remote code execution on the company's SRX firewalls and EX switches.Junos OS is an operating system based on Linux and FreeBSD that runs on Juniper Networks firewalls, network switches and other security devices.

Apple last year introduced a security feature called App Management that's designed to prevent one application from modifying another without authorization under macOS Ventura - but a developer claims it's not very good at its job under some circumstances. "If an app is modified by something that isn't signed by the same development team and isn't allowed by an NSUpdateSecurityPolicy, macOS will block the modification and notify the user that an app wants to manage other apps," explained Justin Sagurton of Apple's privacy engineering team, in a video presentation at the fruity computer seller's 2022 Worldwide Developers Conference.
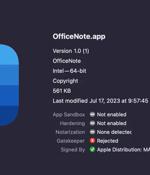
A new variant of an Apple macOS malware called XLoader has surfaced in the wild, masquerading its malicious features under the guise of an office productivity app called "OfficeNote." "The new version of XLoader is bundled inside a standard Apple disk image with the name OfficeNote.dmg," SentinelOne security researchers Dinesh Devadoss and Phil Stokes said in a Monday analysis.

Software services provider Ivanti is warning of a new critical zero-day flaw impacting Ivanti Sentry that it said is being actively exploited in the wild, marking an escalation of its security woes. "If exploited, this vulnerability enables an unauthenticated actor to access some sensitive APIs that are used to configure the Ivanti Sentry on the administrator portal," the company said.

In the modern world it's become increasingly likely that virtual systems and IT-adjacent technologies are utilized to manage and control installed physical security devices, meaning that an effective and safe security system must be designed with input from both physical security and IT teams. In a newly converged cloud-based security system, IT staff may attempt to access and adjust physical security hardware in line with their own set of internal policies, accidentally exposing exploits or vulnerabilities that were previously covered only by physical security protocols.

Visibility into the security posture is critical for staying ahead of the cloud attackers due to the nature of cloud infrastructure. Security mechanisms are usually designed to address security issues in specific technologies.

The U.S. Cybersecurity and Infrastructure Security Agency has added a critical security flaw in Adobe ColdFusion to its Known Exploited Vulnerabilities catalog, based on evidence of active exploitation. The vulnerability, cataloged as CVE-2023-26359, relates to a deserialization flaw present in Adobe ColdFusion 2018 and ColdFusion 2021 that could result in arbitrary code execution in the context of the current user without requiring any interaction.