Security News > 2023 > May

A new malware known as 'LOBSHOT' distributed using Google ads allows threat actors to stealthily take over infected Windows devices using hVNC. Earlier this year, BleepingComputer and numerous cybersecurity researchers reported a dramatic increase in threat actors utilizing Google ads to distribute malware in search results. In a new report by Elastic Security Labs, researchers revealed that a new remote access trojan named LOBSHOT was being distributed through Google Ads.

T-Mobile disclosed the second data breach of 2023 after discovering that attackers had access to the personal information of hundreds of customers for more than a month, starting late February 2023. "In March 2023, the measures we have in place to alert us to unauthorized activity worked as designed and we were able to determine that a bad actor gained access to limited information from a small number of T-Mobile accounts between late February and March 2023," the company said in data breach notification letters sent to affected individuals just before the weekend, on Friday, April 28, 2023.

"There are secrets in Jenkins, secrets in my TerraForm script, in my Infrastructure as a Service script. I have secrets everywhere." The deployment of centralized secrets management solution is arguably the best way to properly address these issues.

Update 5/1/23: Title updated to reflect this bug only allowed the user to see their legacy check. A silly Twitter bug allowed previously-verified accounts to add their legacy 'Blue Check' back to their profile for free.

A silly Twitter bug allowed previously-verified accounts to add their legacy 'Blue Check' back to their profile for free. On April 20th, Twitter finally removed the legacy verified check marks from accounts worldwide that were used to demonstrate the authenticity of accounts belonging to businesses, celebrities, politicians, activists, and journalists.

A silly Twitter bug allows previously-verified accounts to add their legacy 'Blue Check' back to their profile for free. On April 20th, Twitter finally removed the legacy verified check marks from accounts worldwide that were used to demonstrate the authenticity of accounts belonging to businesses, celebrities, politicians, activists, and journalists.
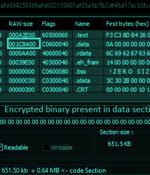
An analysis of over 70 billion DNS records has led to the discovery of a new sophisticated malware toolkit dubbed Decoy Dog targeting enterprise networks. "Decoy Dog is a cohesive toolkit with a number of highly unusual characteristics that make it uniquely identifiable, particularly when examining its domains on a DNS level," Infoblox said in an advisory published late last month.

The leak comes after the threat actor warned Western Digital on April 17th that they would hurt them until they "Cannot stand anymore" if a ransom was not paid. On March 26th, Western Digital suffered a cyberattack where threat actors breached its internal network and stole company data.

In brief You may have heard news this week that Google is finally updating its authenticator app to add Google account synchronization. According to the pair, whose discoveries we've covered in the past, this means the seed used to generate 2FA codes is being transmitted without E2EE and is likely visible to Google when stored on its servers.

In this article, we'll walk through the most essentials questions around the challenge of lateral movement protection, understand why multifactor authentication and service account protection are the gaps that make it possible, and learn how Silverfort's platform turns the tables on attackers and makes lateral movement protection finally within reach. To add another dimension to the lateral movement protection challenge, keep in mind that not all accounts are created equal.