Security News > 2022 > May
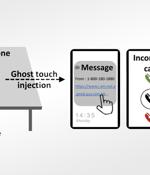
GhostTouch, as it's called, "Uses electromagnetic interference to inject fake touch points into a touchscreen without the need to physically touch it," a group of academics from Zhejiang University and Technical University of Darmstadt said in a new research paper. The core idea is to take advantage of the electromagnetic signals to inject fake touch events such as taps and swipes into targeted locations of the touchscreen with the goal of taking over remote control and manipulating the underlying device.

Akamai has spoken of a distributed denial of service assault against one of its customers during which the attackers astonishingly claimed to be associated with REvil, the notorious ransomware-as-a-service gang. Earlier this month, Akamai's Security Intelligence Response Team got called in to help clean up a Layer 7 attack on one of the vendor's hospitality customers by a group claiming to be connected to REvil.

This is especially critical for mitigating against rising ransomware attacks - a threat that 57% of security leaders expect to be compromised by within the next year. To help you stay ahead, Lookout Chief Strategy Officer, Aaron Cockerill met with Microsoft Chief Security Advisor, Sarah Armstrong-Smith to discuss how remote work and the cloud have made it more difficult to spot a ransomware attack, as well as how deploying behavioral-anomaly-based detection can help mitigate ransomware risk.

Regardless of how centralized or distributed, the weak link appears when private keys or other MPC components must be computationally executed on a CPU. The point of the encryption protocols is that the algorithm is public, and the security relies only on the keys. If an attacker infiltrates multiple hosts, and gains access to the required pieces, they can perform the multi-party computation on their own and steal digital assets and funds.

China has begun talking to ten nations in the South Pacific with an offer to help them improve their network infrastructure, cyber security, digital forensics and other capabilities - all with the help of Chinese tech vendors. That's a nod to accusations that China practices what's been labelled "Debt trap diplomacy" whereby development assistance comes with repayment plans small nations may not be able to afford.

Perforce Software released the results of its annual State of Automotive Software Development survey conducted in partnership with Automotive IQ. Close to 600 automotive development professionals across the globe provided responses to current practices and emerging trends within the industry. Key findings suggest a growing concern for automotive software security, while the automotive vehicle market continues to rapidly evolve.

Zyxel has released patches to address four security flaws affecting its firewall, AP Controller, and AP products to execute arbitrary operating system commands and steal select information. CVE-2022-26531 - Several input validation flaws in command line interface commands for some versions of firewall, AP controller, and AP devices that could be exploited to cause a system crash.

While all markets were united in financial services being the most important sector for robust identity verification, consumers in Mexico believe it is an important step when interacting with sharing economy brands. Where more sensitive personal data is concerned, consumers indicated robust identity verification becomes even more important.

At the Workshop on Offensive Technologies 2022 on Thursday, security researchers demonstrated how to meddle with AirTags, Apple's coin-sized tracking devices. In February, Apple responded to reports of AirTag misuse by announcing various changes intended to make its tracking tokens more difficult to use surreptitiously.

In what is either a creepy, weird spin on Robin Hood or something from a Black Mirror episode, we're told a ransomware gang is encrypting data and then forcing each victim to perform three good deeds before they can download a decryption tool. The so-called GoodWill ransomware group, first identified by CloudSEK's threat intel team, doesn't appear to be motivated by money.