Security News

It's just under two weeks since Google rushed out a Chrome patch for the then-current version 107 to seal off a bug that was already being used in real-life attacks. How might the bug might be triggered? Was merely viewing a booby-trapped web page enough? Could it be abused for remote code execution? Could the crooks end up installing malware without any visible warning? Who was using it? Were they state-sponsored attackers, or some other sort of cybercriminals? What they were after? Were they into data stealing, ransomware attacks, unlawful surveillance, or all of those things?

Search giant Google on Friday released an out-of-band security update to fix a new actively exploited zero-day flaw in its Chrome web browser. The high-severity flaw, tracked as CVE-2022-4262, concerns a type confusion bug in the V8 JavaScript engine.

Google has released Chrome 108.0.5359.94/.95 for Windows, Mac, and Linux users to address a single high-severity security flaw, the ninth Chrome zero-day exploited in the wild patched since the start of the year.This update was immediately rolled out to our systems when BleepingComputer checked for new updates from the Chrome menu > Help > About Google Chrome.
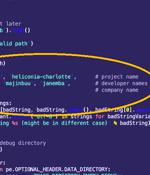
A Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on targeted devices by exploiting several zero-day flaws in Google Chrome, Mozilla Firefox, and Windows, some of which date back to December 2018. "Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox, and Microsoft Defender, and provides all the tools necessary to deploy a payload to a target device," Google Threat Analysis Group researchers Clement Lecigne and Benoit Sevens said in a write-up.
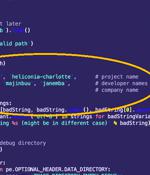
A Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on targeted devices by exploiting several zero-day flaws in Google Chrome, Mozilla Firefox, and Windows, some of which date back to December 2018. "Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox, and Microsoft Defender, and provides all the tools necessary to deploy a payload to a target device," Google Threat Analysis Group researchers Clement Lecigne and Benoit Sevens said in a write-up.

Zero-days are bugs for which there were zero days you could have updated proactively. Because cybercriminals not only found the bug first, but also figured out how to exploit it for nefarious purposes before a patch was prepared and published.

Google on Thursday released software updates to address yet another zero-day flaw in its Chrome web browser. Clement Lecigne of Google's Threat Analysis Group has been credited with reporting the flaw on November 22, 2022.

Google has released an emergency security update for the desktop version of the Chrome web browser, addressing the eighth zero-day vulnerability exploited in attacks this year.As users need time to apply the security update on their Chrome installations, Google has withheld details about the vulnerability to prevent expanding its malicious exploitation.

This Mark of the Web is an alternate data stream that contains information about the file, such as the URL security zone the file originates from, its referrer, and its download URL. When a user attempts to open a file with a MoTW attribute, Windows will display a security warning asking if they are sure they wish to open the file. After analyzing the files, Will Dormann, a senior vulnerability analyst at ANALYGENCE, discovered that the threat actors were using a new Windows zero-day vulnerability that prevented Mark of the Web security warnings from being displayed.

Photos: IRISSCON 2022IRISSCON, the annual cyber crime-themed conference organized by the Irish Reporting and Information Security Service, was held in Dublin, Ireland on Thursday, November 10, 2022. Security "Sampling" puts US federal agencies at riskTitania launched an independent research report that uncovers the impact of exploitable misconfigurations on the security of networks in the US federal government.