Security News

A critical zero-day vulnerability in all versions of Exim mail transfer agent software can let unauthenticated attackers gain remote code execution on Internet-exposed servers. MTA servers like Exim are highly vulnerable targets, primarily because they are often accessible via the Internet, serving as easy entry points for attackers into a target's network.

Google and Mozilla have patched a zero-day exploit in Chrome and Firefox, respectively. The zero-day exploit could leave users open to a heap buffer overflow, through which attackers could inject malicious code.

Cisco warned customers on Wednesday to patch a zero-day IOS and IOS XE software vulnerability targeted by attackers in the wild."An attacker could exploit this vulnerability by either compromising an installed key server or modifying the configuration of a group member to point to a key server that is controlled by the attacker," Cisco explained in a security advisory published on Wednesday.

Google has fixed another critical zero-day vulnerability in Chrome that is being exploited in the wild. The vulnerability is caused by a heap buffer overflow in vp8 encoding in libvpx - a video codec library from Google and the Alliance for Open Media.

Google on Wednesday rolled out fixes to address a new actively exploited zero-day in the Chrome browser. Tracked as CVE-2023-5217, the high-severity vulnerability has been described as a...

Google has patched the fifth Chrome zero-day vulnerability exploited in attacks since the start of the year in emergency security updates released today. Today, Google TAG's Maddie Stone revealed that the CVE-2023-5217 zero-day vulnerability was exploited to install spyware.

The Chrome zero-day exploited in the wild and patched by Google a few weeks ago has a new ID and a description that tells the whole story: the vulnerability is not in Chrome, but the libwebp library, which is used by many popular applications for encoding/decoding the WebP image format.The source of the vulnerability is a flawed implementation of the Huffman coding algorithm, which may allow attackers to trigger a heap buffer overflow and to execute arbitrary code.
The three zero-day flaws addressed by Apple on September 21, 2023, were leveraged as part of an iPhone exploit chain in an attempt to deliver a spyware strain called Predator targeting former...

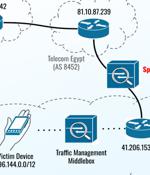
Security researchers with The Citizen Lab and Google's Threat Analysis Group revealed today that three zero-days patched by Apple on Thursday were abused as part of an exploit chain to install Cytrox's Predator spyware. Google TAG also observed the attackers using a separate exploit chain to drop Predator spyware on Android devices in Egypt, exploiting CVE-2023-4762-a Chrome bug patched on September 5th-as a zero-day to gain remote code execution.

Apple has released updates for iOS and iPadOS, macOS, watchOS, and Safari to fix three zero-day vulnerabilities exploited "Against versions of iOS before iOS 16.7.". Earlier this month, Apple closed two zero-day vulnerabilities that have been chained together by attackers to deliver NSO Group's Pegasus spyware.