Security News

The Raspberry Robin worm has been used in attacks against telecommunications and government office systems across Latin America, Australia, and Europe since at least September 2022. "The main payload itself is packed with more than 10 layers for obfuscation and is capable of delivering a fake payload once it detects sandboxing and security analytics tools," Trend Micro researcher Christopher So said in a technical analysis published Tuesday.

The Raspberry Robin malware is now trying its hand at some trickery by dropping a fake payload to confuse researchers and evade detection when it detects it's being run within sandboxes and debugging tools. Raspberry Robin is a worm-like malware dropper that sells initial access to compromised networks to ransomware gangs and malware operators.
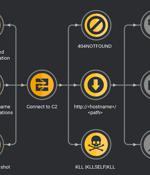
Cybersecurity researchers have reported an increase in TrueBot infections, primarily targeting Mexico, Brazil, Pakistan, and the U.S. Cisco Talos said the attackers behind the operation have moved from using malicious emails to alternative delivery methods such as the exploitation of a now-patched remote code execution flaw in Netwrix auditor as well as the Raspberry Robin worm. TrueBot is a Windows malware downloader that's attributed to a threat actor tracked by Group-IB as Silence, a Russian-speaking crew believed to share associations with Evil Corp and TA505.

December 2022 sees the 35th anniversary of the first major self-spreading computer virus - the infamous CHRISTMA EXEC worm that temporarily crushed the major mainframe networks of the day. Not by any deliberately coded side-effects such as file scrambling or data deletion, but simply by leeching too much network bandwidth for its own unauthorised purpose.

Raspberry Robin, a worm that spreads through Windows systems via USB drives, has rapidly evolved: now backdoor access is being sold or offered to infected machines so that ransomware, among other code, can be installed by cybercriminals. In a report on Thursday, Microsoft's Security Threat Intelligence unit said Raspberry Robin is now "Part of a complex and interconnected malware ecosystem" with links to other families of malicious code and ties to ransomware infections.

Microsoft says a threat group tracked as DEV-0950 used Clop ransomware to encrypt the network of a victim previously infected with the Raspberry Robin worm. "Beginning on September 19, 2022, Microsoft identified Raspberry Robin worm infections deploying IcedID and-later at other victims-Bumblebee and TrueBot payloads," Microsoft Security Threat Intelligence analysts said.

Microsoft on Friday disclosed a potential connection between the Raspberry Robin USB-based worm and an infamous Russian cybercrime group tracked as Evil Corp. The tech giant said it observed the FakeUpdates malware being delivered via existing Raspberry Robin infections on July 26, 2022. Raspberry Robin, also called QNAP Worm, is known to spread from a compromised system via infected USB devices containing malicious a.LNK files to other devices in the target network.

Cybersecurity researchers are drawing attention to an ongoing wave of attacks linked to a threat cluster tracked as Raspberry Robin that's behind a Windows malware with worm-like capabilities. The infections involve a worm that propagates over removable USB devices containing malicious a.LNK file and leverages compromised QNAP network-attached storage devices for command-and-control.

Contrary to most worms, Hopper was built to do good. The development team at Cymulate based Hopper on a common malware stager - a small executable that serves as an initial payload, with its primary objective being to prepare a larger payload. Our stager also serves as a PE packer, a program that loads and executes programs indirectly, usually from a package.

Microsoft says that a recently spotted Windows worm has been found on the networks of hundreds of organizations from various industry sectors. Cybersecurity firm Sekoia also observed it using QNAP NAS devices as command and control servers servers in early November [PDF], while Microsoft said it found malicious artifacts linked to this worm created in 2019.