Security News

The WordPress plugin WP Fastest Cache is vulnerable to an SQL injection vulnerability that could allow unauthenticated attackers to read the contents of the site's database. WP Fastest Cache is a caching plugin used to speed up page loads, improve visitor experience, and boost the site's ranking on Google search.

A critical severity vulnerability impacting Royal Elementor Addons and Templates up to version 1.3.78 is reported to be actively exploited by two WordPress security teams. Two WordPress security firms, Wordfence and WPScan, have marked CVE-2023-5360 as actively exploited since August 30, 2023, with the attack volume ramping up starting on October 3, 2023.
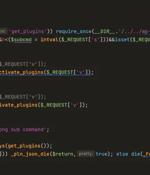
Cybersecurity researchers have shed light on a new sophisticated strain of malware that masquerades a WordPress plugin to stealthily create administrator accounts and remotely control a...

A new malware has been posing as a legitimate caching plugin to target WordPress sites, allowing threat actors to create an administrator account and control the site's activity. The malware is a backdoor with a variety of functions that let it manage plugins and hide itself from active ones on the compromised websites, replace content, or redirect certain users to malicious locations.

More than 17,000 WordPress websites have been compromised in the month of September 2023 with malware known as Balada Injector, nearly twice the number of detections in August. Of these, 9,000 of...

Multiple Balada Injector campaigns have compromised and infected over 17,000 WordPress sites using known flaws in premium theme plugins. Balada Injector is a massive operation discovered in December 2022 by Dr. Web, which has been leveraging various exploits for known WordPress plugin and theme flaws to inject a Linux backdoor.

All-in-One WP Migration, a popular data migration plugin for WordPress sites with 5 million active installations, suffers from unauthenticated access token manipulation that could allow attackers to access sensitive site information. All-in-One WP Migration is a user-friendly WordPress site migration tool for non-technical and inexperienced users, allowing seamless exports of databases, media, plugins, and themes into a single archive that is easy to restore on a new destination.

Two vulnerabilities affecting some version of Jupiter X Core, a premium plugin for setting up WordPress and WooCommerce websites, allow hijacking accounts and uploading files without authentication. Jupiter X Core is an easy-to-use yet powerful visual editor, part of the Jupiter X theme, which is used in over 172,000 websites.

According to Colorlib, WordPress is used by over 800 million websites worldwide. It is vital to protect your WordPress site and your data, readers, users and company by regularly auditing your WordPress site's security configurations.

Popular WordPress form-building plugin Ninja Forms contains three vulnerabilities that could allow attackers to achieve privilege escalation and steal user data. The second and third problems, tracked as CVE-2023-38393 and CVE-2023-38386, respectively, are broken access control issues on the plugin's form submissions export feature, allowing Subscribers and Contributors to export all of the data that users have submitted on the impacted WordPress site.