Security News

Microsoft says Windows Server updates released during December's Patch Tuesday will trigger errors when trying to create new virtual machines on some Hyper-V hosts. [...]

Microsoft has revoked several Microsoft hardware developer accounts after drivers signed through their profiles were used in cyberattacks, including ransomware incidents. "Microsoft was informed that drivers certified by Microsoft's Windows Hardware Developer Program were being used maliciously in post-exploitation activity. In these attacks, the attacker had already gained administrative privileges on compromised systems prior to use of the drivers," explains the advisory from Microsoft.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.
Google has officially begun rolling out support for passkeys, the next-generation passwordless login standard, to its stable version of Chrome web browser. This calls for websites to build passkey support on their sites using the WebAuthn API. Essentially, the technology works by creating a unique cryptographic key pair to associate with an account for the app or website during account registration.

Microsoft is finally adding a built-in screen recorder to Windows 11 through the Snipping Tool, enabling users to capture videos of their desktop without the need for a third-party app. The update is being pushed as part of a phased roll-out to Windows Insiders in the Dev Channel and will be available once Snipping Tool version 11.2211.35.0 is installed.

Microsoft Edge will drop support for Windows 7 and Windows 8/8.1 after the release of version 109 on January 12th, 2023. The decision to no longer provide Windows 7 / 8.1 support for Edge users almost perfectly aligns with the end of support for Windows 7 Extended Security Update and Windows 8/8.1 on January 10th, 2023.

To help combat the constant risk of password theft, Microsoft added phishing protection in Windows 11 Version 22H2. When enabled, Enhanced Phishing Protection is offered through Microsoft Defender SmartScreen. If Enhanced Phishing Protection detects a user entered their Windows password into a website or an application, an alert and prompt are shown warning the user to change their password.
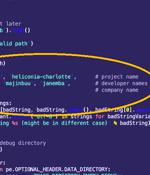
A Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on targeted devices by exploiting several zero-day flaws in Google Chrome, Mozilla Firefox, and Windows, some of which date back to December 2018. "Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox, and Microsoft Defender, and provides all the tools necessary to deploy a payload to a target device," Google Threat Analysis Group researchers Clement Lecigne and Benoit Sevens said in a write-up.
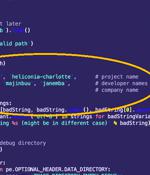
A Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on targeted devices by exploiting several zero-day flaws in Google Chrome, Mozilla Firefox, and Windows, some of which date back to December 2018. "Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox, and Microsoft Defender, and provides all the tools necessary to deploy a payload to a target device," Google Threat Analysis Group researchers Clement Lecigne and Benoit Sevens said in a write-up.