Security News

Microsoft has released the Windows 11 22H2 KB5030219 cumulative update to fix security vulnerabilities and introduce 24 changes, improvements, and bug fixes. KB5030219 is a mandatory Windows 11 cumulative update containing the September 2023 Patch Tuesday security updates.

In 2017, Microsoft added a feature to its Windows 10 operating system: S mode, a stripped-down, tightly-locked and low-end way to run Windows 10 and the Home edition of Windows 11 that is still PC friendly. S mode is available for Windows Home Edition for Windows 10 and 11 as well as Windows 10 Pro and Windows 10 Education.

Microsoft will block third-party printer driver delivery in Windows Update as part of a substantial and gradual shift in its printer driver strategy over the next 4 years. "With the release of Windows 10 21H2, Windows offers inbox support for Mopria compliant printer devices over network and USB interfaces via the Microsoft IPP Class Driver," Microsoft says.
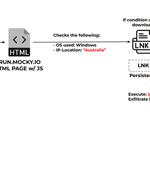
A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool to plunder NTLMv2 hashes from compromised Windows systems primarily located in Australia, Poland, and Belgium. "In this campaign, the threat actors steal and exfiltrate NTLMv2 hashes using customized versions of Nishang's Start-CaptureServer PowerShell script, executing various system commands, and exfiltrating the retrieved data via Mockbin APIs," security researchers Niraj Shivtarkar and Avinash Kumar said.

Microsoft is rolling out a new version of the Paint application on Windows 11 Insider builds that can remove the background from any picture with the click of a button. You can see a demonstration of the background removal below using the Windows wallpaper.

Cybercriminals are leveraging a legitimate Windows tool called 'Advanced Installer' to infect the computers of graphic designers with cryptocurrency miners. The attackers promote installers for popular 3D modeling and graphic design software such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, likely through black hat search engine optimization techniques.

Microsoft says Storm-0558 Chinese hackers stole a signing key used to breach government email accounts from a Windows crash dump after compromising a Microsoft engineer's corporate account. While investigating Storm-0558's attack, Microsoft found that the MSA key was leaked into a crash dump after a consumer signing system crashed in April 2021.

MSI has released BIOS updates to fix a known issue that triggers blue screens of death on Windows computers after installing August 2023 preview updates. "The new BIOS coming will include an update on the Intel CPU uCode which will prevent any more messages regarding the 'UNSUPPORTED PROCESSOR' issues. This upcoming update will correspond to both 13th-generation and newer ones," MSI said on Wednesday.

The risk of running obsolete code and hardware was highlighted after attackers exfiltrated data from a UK supplier of high-security fencing for military bases. The initial entry point? A Windows 7 PC. While the supplier, Wolverhampton-based Zaun, said it believed that no classified information was downloaded, reports indicated that attackers were able to obtain data that could be used to gain access to some of the UK's most sensitive military and research sites.

Microsoft has reminded users that TLS 1.0 and 1.1 will soon be disabled by default in Windows. SQL Server 2008 R2 finally dropped out of Extended Security Updates in July, although Microsoft has published instructions for adding TLS 1.2 support.