Security News

Acting now will almost certainly jump you ahead of the many inquisitive cybercriminals out there, given that none of the bugs patched in this update seem to be zero-day security holes. Both CVE-2022-22040 and CVE-2022-22021 are annotated with the comment that "a malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine's VMX process running on the host."

VMware has issued a critical security update to address issues in its ESXi, Fusion and Workstation products, including VMware Cloud Foundation versions. VMware noted that patching VMware ESXi, Fusion and Workstation is the fastest method to resolve the issues, but organizations could also remove USB controllers from their VMs as a workaround.

An initial access broker group tracked as Prophet Spider has been linked to a set of malicious activities that exploits the Log4Shell vulnerability in unpatched VMware Horizon Servers. The payloads observed include cryptocurrency miners, Cobalt Strike Beacons, and web shells, corroborating a previous advisory from the U.K. National Health Service that sounded the alarm on active exploitation of the vulnerabilities in VMware Horizon servers to drop malicious web shells and establish persistence on affected networks for follow-on attacks.

LockBit is the latest ransomware gang whose Linux encryptor has been discovered to be focusing on the encryption of VMware ESXi virtual machines.Due to this, ransomware gangs have evolved their tactics to create Linux encryptors that specifically target the popular VMware vSphere and ESXi virtualization platforms over the past year.

VMware urges customers to patch critical Log4j security vulnerabilities impacting Internet-exposed VMware Horizon servers targeted in ongoing attacks. Microsoft also warned two weeks ago of a Chinese-speaking threat actor tracked as DEV-0401 who deploys Night Sky ransomware on Internet-exposed VMware Horizon servers using Log4Shell exploits.

Organizations running sophisticated virtual networks with VMware's vSphere service are actively being targeted by cryptojackers, who have figured out how to inject the XMRig commercial cryptominer into the environment, undetected.Uptycs' Siddharth Sharma has released research showing threat actors are using malicious shell scripts to make modifications and run the cryptominer on vSphere virtual networks.

The Night Sky ransomware gang has started to exploit the critical CVE-2021-44228 vulnerability in the Log4j logging library, also known as Log4Shell, to gain access to VMware Horizon systems. Spotted in late December 2021 by security researcher MalwareHunterTeam, Night Sky ransomware focuses on locking enterprise networks.

AvosLocker is the latest ransomware gang that has added support for encrypting Linux systems to its recent malware variants, specifically targeting VMware ESXi virtual machines. While we couldn't find what targets were targeted using this AvosLocker ransomware Linux variant, BleepingComputer knows of at least one victim that got hit with a $1 million ransom demand.
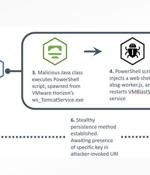
The digital security team at the U.K. National Health Service has raised the alarm on active exploitation of Log4Shell vulnerabilities in unpatched VMware Horizon servers by an unknown threat actor to drop malicious web shells and establish persistence on affected networks for follow-on attacks. "The attack likely consists of a reconnaissance phase, where the attacker uses the Java Naming and Directory InterfaceTM via Log4Shell payloads to call back to malicious infrastructure," the non-departmental public body said in an alert.

UK's National Health Service has published a cyber alert warning of an unknown threat group targeting VMware Horizon deployments with Log4Shell exploits. According to the NHS notice, the actor is leveraging the exploit to achieve remote code execution on vulnerable VMware Horizon deployments on public infrastructure.