Security News

Ukrainian radio operator TAVR Media on Thursday became the latest victim of a cyberattack, resulting in the broadcast of a fake message that President Volodymyr Zelenskyy was seriously ill. "Cybercriminals spread information that the President of Ukraine, Volodymyr Zelenskyy, is allegedly in intensive care, and his duties are performed by the Chairman of the Verkhovna Rada, Ruslan Stefanchuk," the State Service of Special Communications and Information Protection of Ukraine said in an update.

On Thursday, Ukrainian media group TAVR Media confirmed that it was hacked to spread fake news about President Zelenskiy being in critical condition and under intensive care. SSSCIP added that the attackers breached TAVR Media's servers and broadcasting systems to spread fake news suggesting that the Ukrainian President is allegedly under intensive care, in critical condition, with Parliament Chairman Ruslan Stefanchuk acting in his stead. Zelenskyi also refuted the reports in a video shared on his official Instagram account, saying they were fake news spread by Russian-linked threat actors.

A large software development company whose software is used by different state entities in Ukraine was at the receiving end of an "Uncommon" piece of malware, new research has found. The malware, first observed on the morning of May 19, 2022, is a custom variant of the open source backdoor known as GoMet and is designed for maintaining persistent access to the network.
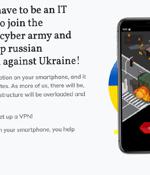
Russian threat actors capitalized on the ongoing conflict against Ukraine to distribute Android malware camouflaged as an app for pro-Ukrainian hacktivists to launch distributed denial-of-service attacks against Russian sites. "The apps were not distributed through the Google Play Store, but hosted on a domain controlled by the actor and disseminated via links on third party messaging services."

Google's Threat Analysis Group, whose primary goal is to defend Google users from state-sponsored attacks, said today that Russian-backed threat groups are still focusing their attacks on Ukrainian organizations. In a report regarding recent cyber activity in Eastern Europe, Google TAG security engineer Billy Leonard revealed that hackers part of the Turla Russian APT group have also been spotted deploying their first Android malware.
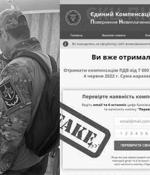
The Cyber Police of Ukraine last week disclosed that it apprehended nine members of a criminal gang that embezzled 100 million hryvnias via hundreds of phishing sites that claimed to offer financial assistance to Ukrainian citizens as part of a campaign aimed at capitalizing on the ongoing conflict. "Criminals created more than 400 phishing links to obtain bank card data of citizens and appropriate money from their accounts," the agency said in a press statement last week.

Scammers are claiming to be collecting donations to help Ukrainian refugees and war victims while impersonating legitimate Ukrainian humanitarian aid organizations, according to the Federal Bureau of Investigation. "The FBI warns the public of fraudulent schemes seeking donations or other financial assistance related to the crisis in Ukraine," the US law enforcement agency said this week in a public service announcement.

A 28-year-old Ukrainian national has been sentenced to four years in prison for siphoning thousands of server login credentials and selling them on the dark web for monetary gain as part of a credential theft scheme. The illegal sale involved the trafficking of login credentials to servers located across the world and personally identifiable information such as dates of birth and Social Security numbers belonging to U.S. residents on a darknet marketplace.

A Ukrainian man has been sentenced to four years in a US federal prison for selling on a dark-web marketplace stolen login credentials for more than 6,700 compromised servers. The prosecution's documents [PDF] detail an unnamed, dark-web marketplace on which usernames and passwords along with personal data, including more than 330,000 dates of birth and social security numbers belonging to US residents, were bought and sold illegally.

Glib Oleksandr Ivanov-Tolpintsev, a 28-year-old from Ukraine, was sentenced today to 4 years in prison for stealing thousands of login credentials per week and selling them on a dark web marketplace. "From 2017 through 2019, Ivanov-Tolpintsev listed for sale thousands of login credentials of servers on the Marketplace, including more than 100 in the Middle District of Florida."