Security News
Amid the ongoing war between Russia and Ukraine, government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea have been attacked as part of an active campaign that drops a previously unseen, modular framework dubbed CommonMagic. "Although the initial vector of compromise is unclear, the details of the next stage imply the use of spear phishing or similar methods," Kaspersky said in a new report.

You've almost certainly heard of the ransomware family known as DoppelPaymer, if only because the name itself is a reminder of the double-barrelled blackmail technique used by many contemporary ransomware gangs. The good news, if you can call it that, is the reason why Europol is writing about the DoppelPaymer ransomware right now.

Law enforcement authorities from Germany and Ukraine have targeted suspected core members of a cybercrime group that has been behind large-scale attacks using DoppelPaymer ransomware. Both individuals are believed to have taken up crucial positions in the DoppelPaymer group.

"The consequences of Russia's war against Ukraine have ushered in a new era of volatility and unpredictability for global cybercrime that carries a multitude of implications for defenders," Leslie said. Russian cybercrime, per the report, refers to a diverse group or Russian-speaking miscreants located in Russia, Ukraine, Belarus, the Baltics, the South Caucasus, and Central Asia.

The Computer Emergency Response Team of Ukraine says Russian state hackers have breached multiple government websites this week using backdoors planted as far back as December 2021. CERT-UA spotted the attacks after discovering a web shell on Thursday morning on one of the hacked websites that the threat actors used to install additional malware.

The Aspen Institute has published a good analysis of the successes, failures, and absences of cyberattacks as part of the current war in Ukraine: "The Cyber Defense Assistance Imperative Lessons from Ukraine." As a result, it is timely to assess how to provide organized, effective cyber defense assistance to safeguard the post-war order from potential aggressors.

Millions of Russians in almost a dozen cities throughout the country were greeted Wednesday morning by radio alerts, text messages, and sirens warning of an air raid or missile strikes that never occurred. According to reports from news operations in Russia, a woman's voice was broadcast through a number of radio stations - including Relax FM, Avatoradio, Yumor FM, and Comedy Radio - saying, "Attention, an air raid warning is being announced. Go to the shelter immediately. Attention, Attention, threat of a missile strike."

Russia's cyber attacks against Ukraine surged by 250% in 2022 when compared to two years ago, Google's Threat Analysis Group and Mandiant disclosed in a new joint report. Mandiant said it observed, "More destructive cyber attacks in Ukraine during the first four months of 2022 than in the previous eight years with attacks peaking around the start of the invasion."

Russia's invasion of Ukraine continues to have a major impact on energy prices, inflation, and cyberthreats, with the ransomware scene experiencing some of the biggest shifts, according to ESET. "The ongoing war in Ukraine has created a divide among ransomware operators, with some supporting and others opposing the aggression. Attackers have also been using increasingly destructive tactics, such as deploying wipers that mimic ransomware and encrypt the victim's data with no intention of providing a decryption key," explains Roman Kováč, Chief Research Officer at ESET. The digital threats trends. The war also affected brute-force attacks against exposed RDP services, but despite the decline of these attacks in 2022, password guessing remains the most favored network attack vector.

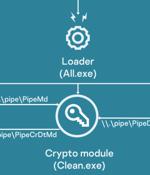
A Russia-linked threat actor has been observed deploying a new information-stealing malware in cyber attacks targeting Ukraine. Dubbed Graphiron by Broadcom-owned Symantec, the malware is the handiwork of an espionage group known as Nodaria, which is tracked by the Computer Emergency Response Team of Ukraine as UAC-0056.