Security News

In a first for a major Chinese tech company, drone-maker DJI Technologies announced on Tuesday that it will temporarily suspend business in both Russia and Ukraine. "DJI is internally reassessing compliance requirements in various jurisdictions. Pending the current review, DJI will temporarily suspend all business activities in Russia and Ukraine. We are engaging with customers, partners and other stakeholders regarding the temporary suspension of business operations in the affected territories," declared DJI in a canned statement.

DDoS attacks were at all-time high in Q1 2022 due to war in Ukraine. Kaspersky recently released findings that the number of DDoS attacks are the most frequent they have ever been and dwarf the rate of DDoS attacks from just a year prior.

Shuckworm's attacks are part of an ongoing campaign by Russian state-sponsored threat groups that escalated their efforts in the run-up to the invasion of Ukraine in late February, and have continue their attacks since. The Security Service of Ukraine last year said the group was responsible for more than 5,000 attacks against public agencies or critical infrastructure and linked Shuckworm to the FSB, Russia's security service and successor to the KGB. The SSU said the group targeted more than 1,500 government computer systems over seven years.

Threat analysts report that the Russian state-sponsored threat group known as Gamaredon is launching attacks against targets in Ukraine using new variants of the custom Pteredo backdoor. According to a report by Symantec, who tracks the group as Shuckworm, the actor is currently using at least four variants of the "Pteredo" malware, also tracked as Pteranodon.

"The attackers attempted to take down several infrastructure components of their target, namely: Electrical substations, Windows-operated computing systems, Linux-operated server equipment, [and] active network equipment," The State Service of Special Communications and Information Protection of Ukraine said in a statement. Slovak cybersecurity firm ESET, which collaborated with CERT-UA to analyze the attack, said the attempted intrusion involved the use of ICS-capable malware and regular disk wipers, with the adversary unleashing an updated variant of the Industroyer malware, which was first deployed in a 2016 assault on Ukraine's power grid.

The Computer Emergency Response Team of Ukraine, with the help of ESET and Microsoft security experts, has thwarted a cyber attack by the Sandworm hackers, who tried to shut down electrical substations run by an energy provider in Ukraine. "We assess with high confidence that the attackers used a new version of the Industroyer malware, which was used in 2016 to cut power in Ukraine."

In a blog post outlining the actions, Microsoft reported attackers used the domains to target Ukrainian media organizations, government institutions and foreign policy think tanks based in the U.S. and Europe. "We obtained a court order authorizing us to take control of seven internet domains Strontium was using to conduct these attacks," said Tom Burt, corporate vice president of Customer Security and Trust at Microsoft.

Microsoft on Thursday disclosed that it obtained a court order to take control of seven domains used by APT28, a state-sponsored group operated by Russia's military intelligence service, with the goal of neutralizing its attacks on Ukraine. "We have since re-directed these domains to a sinkhole controlled by Microsoft, enabling us to mitigate Strontium's current use of these domains and enable victim notifications," Tom Burt, Microsoft's corporate vice president of customer security and trust, said.

Cyberattacks took down Finnish government websites on Friday while Ukrainian President Volodymyr Zelenskyy addressed Finland's members of parliament. Denial-of-service attacks hit Finland's ministries of Defense and Foreign Affairs' websites around noon local time.
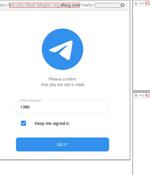
Ukraine's technical security and intelligence service is warning of a new wave of cyber attacks that are aimed at gaining access to users' Telegram accounts. "The criminals sent messages with malicious links to the Telegram website in order to gain unauthorized access to the records, including the possibility to transfer a one-time code from SMS," the State Service of Special Communication and Information Protection of Ukraine said in an alert.