Security News
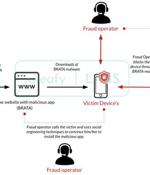
The Android malware tracked as BRATA has been updated with new features that grants it the ability to track device locations and even perform a factory reset in an apparent bid to cover up fraudulent wire transfers. "What makes Android RAT so interesting for attackers is its capability to operate directly on the victim devices instead of using a new device," Cleafy researchers noted in December 2021.

New variants of the BRATA banking trojan have been targeting global Android devices since November with advanced features, including the ability to wipe devices after stealing user data, tracking devices via GPS, and novel obfuscation techniques, researchers have found. The Cleafy team has identified three new variants of BRATA that have been delivered via two new waves of samples in the last few months, researchers reported.

Since December 2021, a growing trend in phishing campaigns has emerged that uses malicious PowerPoint documents to distribute various types of malware, including remote access and information-stealing trojans. According to a report by Netskope's Threat Labs shared with Bleeping Computer before publication, the actors are using PowerPoint files combined with legitimate cloud services that host the malware payloads.
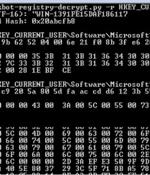
Cybersecurity researchers have decoded the mechanism by which the versatile Qakbot banking trojan handles the insertion of encrypted configuration data into the Windows Registry. Although mainly fashioned as an information-stealing malware, Qakbot has since shifted its goals and acquired new functionality to deliver post-compromise attack platforms such as Cobalt Strike Beacon, with the final objective of loading ransomware on infected machines.

The actors have set up a page that looks very close to Android's official Google Play app store to trick visitors into thinking they are installing the app from a trustworthy service. The malware pretends to be the official banking app for Itaú Unibanco and features the same icon as the legitimate app.

Customers of Chase, Wells Fargo, Bank of America and Capital One, along with nearly 400 other financial institutions, are being targeted by a malicious app disguised to look like the official account management platform for French telecom company Orange S.A. Researchers say this is just the beginning. Once downloaded, the malware - a variant of banking trojan Anubis - steals the user's personal data to rip them off, researchers at Lookout warned in a new report.

Infection chains associated with the multi-purpose Qakbot malware have been broken down into "Distinct building blocks," an effort that Microsoft said will help to detect and block the threat in an effective manner proactively. The Microsoft 365 Defender Threat Intelligence Team dubbed Qakbot a "Customizable chameleon that adapts to suit the needs of the multiple threat actor groups that utilize it."

The initial apps in Google Play were safe, but the creators found a way around the Play Store's protections to install malware on Android users' devices. A November report from ThreatFabric revealed that more than 300,000 Android users unknowingly downloaded malware with banking trojan capabilities, and that it bypassed the Google Play Store restrictions.

Four different Android banking trojans were spread via the official Google Play Store between August and November 2021, resulting in more than 300,000 infections through various dropper apps that posed as seemingly harmless utility apps to take full control of the infected devices. While Google earlier this month instituted limitations to restrict the use of accessibility permissions that allow malicious apps to capture sensitive information from Android devices, operators of such apps are increasingly refining their tactics by other means even when forced to choose the more traditional way of installing apps through the app marketplace.

Overcoming Google Play app restrictions, attackers have successfully racked up more than 300,000 banking trojan installations over just the past four months in the official Android app marketplace. Researchers from Threat Fabric reported that these threat groups have honed their ability to use Google Play to propagate banking trojans by shrinking the footprint of their dropper apps, eliminating the number of permissions they ask for, boosting the overall quality of the attack with better code and standing up convincing companion websites.