Security News
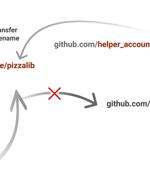
Cloud-based repository hosting service GitHub has addressed a high-severity security flaw that could have been exploited to create malicious repositories and mount supply chain attacks. The RepoJacking technique, disclosed by Checkmarx, entails a bypass of a protection mechanism called popular repository namespace retirement, which aims to prevent developers from pulling unsafe repositories with the same name.

Software supply chains at risk: The account takeover threat. A software supply chain attack consists of targeting software repositories or download locations, in order to spread malware instead of or in addition to legitimate software.

Account takeover attacks on the rise, impacting almost 25% of people in the US. Account takeover attacks can devastate individuals and organizations alike. In a report released Thursday, fraud management company SEON looks at the rise in account takeovers and offers advice to businesses and consumers on how to protect their accounts.

Many cyberattacks begin with the same weakness: user accounts. More specifically, they exploit user credentials, with 89% of web application attacks in 2021 involving stolen or misused usernames and passwords.

Miscreants have reportedly scanned almost 1.6 million websites in attempts to exploit an arbitrary file upload vulnerability in a previously disclosed buggy WordPress plugin. Wordfence disclosed the flaw almost three months ago, and in a new advisory this week warned that criminals are increasing attacks - the WordPress security shop claims it blocked an average of 443,868 attack attempts per day on its customers' sites.

The popular protocol for radio controlled aircraft called ExpressLRS can be hacked in only a few steps, according to a bulletin published last week. The vulnerability in the protocol is tied to the fact some of the information sent over via over-the-air packets is link data that a third-party can use to hijack the connection between drone operator and drone.

A new DFSCoerce Windows NTLM relay attack has been discovered that uses MS-DFSNM, Microsoft's Distributed File System, to completely take over a Windows domain. This service is vulnerable to NTLM relay attacks, which is when threat actors force, or coerce, a domain controller to authenticate against a malicious NTLM relay under an attacker's control.

GitLab has moved to address a critical security flaw in its service that, if successfully exploited, could result in an account takeover. The security flaw affects all versions of GitLab Enterprise Edition starting from 11.10 before 14.9.5, all versions starting from 14.10 before 14.10.4, and all versions starting from 15.0 before 15.0.1.

A critical privilege escalation flaw found in two themes used by more than 90,000 WordPress sites can allow threat actors to take over the sites completely, researchers have found. WordFence Threat Intelligence Team researcher Ramuel Gall discovered the flaw, one of five vulnerabilities he found between early April and early May in the Jupiter and JupiterX Premium WordPress themes, he revealed in a blog post published Wednesday.

The maintainers of the RubyGems package manager have addressed a critical security flaw that could have been abused to remove gems and replace them with rogue versions under specific circumstances. "Due to a bug in the yank action, it was possible for any RubyGems.org user to remove and replace certain gems even if that user was not authorized to do so," RubyGems said in a security advisory published on May 6, 2022.