Security News

The United States Department of Justice has unsealed a pair of indictments that detail alleged Russian government hackers' efforts to use supply chain attacks and malware in an attempt to compromise and control critical infrastructure around the world - including at least one nuclear power plant. The trio allegedly spent 2012 to 2014 working on a project code-named "Dragonfly" during which a supply chain attack targeted updates of industrial control systems and supervisory control and data acquisition systems.

On Friday, Bridgestone Corp. admitted that a subsidiary experienced a ransomware attack in February, prompting it to shut down the computer network and production at its factories in North and Middle America for about a week, said Reuters. Manufacturers like Toyota, already hampered by supply chain shortages, are proving to be particularly attractive targets for ransomware groups.
With so many security and developer teams doing post mortems on the Log4j security vulnerability fiasco that unfolded in late 2021, just 10 days before Christmas, the main question is: how do we avoid this type of pain in the future? The answer is it's complicated. On the upside the pain of that experience has triggered a major software supply-chain security rethink from developers and security teams.

Russia says some of its federal agencies' websites were compromised in a supply chain attack on Tuesday after unknown attackers hacked the stats widget used to track the number of visitors by multiple government agencies. The list of sites impacted in the attack includes the websites of the Energy Ministry, the Federal State Statistics Service, the Federal Penitentiary Service, the Federal Bailiff Service, the Federal Antimonopoly Service, the Culture Ministry, and other Russian state agencies.

As many as seven security vulnerabilities have been disclosed in PTC's Axeda software that could be weaponized to gain unauthorized access to medical and IoT devices. Collectively called "Access:7," the weaknesses - three of which are rated Critical in severity - potentially affect more than 150 device models spanning over 100 different manufacturers, posing a significant supply chain risk.

Digital supply chain risk a new security threat for 2022. Gartner has identified digital supply chain risk as a new security threat and one of its top seven security and risk management trends for 2022.

The global digital supply chain market was pegged at $3.91 billion in 2020, and is expected to reach $13.67 billion by 2030, growing at a CAGR of 13.2% from 2021 to 2030, according to Allied Market Research. Increase in demand for reliable, fast, and effective order execution, rise in demand for cloud-based supply chain management solutions, and improved use of industrial-grade digital technology drive the growth of the global digital supply chain market.
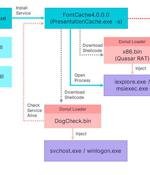
An advanced persistent threat group operating with objectives aligned with the Chinese government has been linked to an organized supply chain attack on Taiwan's financial sector. The second wave of attacks hit a peak between February 10 and 13, 2022, according to a new report published by Taiwanese cybersecurity firm CyCraft, which said the wide-ranging supply chain compromise specifically targeted the software systems of financial institutions, resulting in "Abnormal cases of placing orders."

ActiveState announced the results of its survey, providing insights into the security challenges of the software industry's open source supply chain, which includes the security of open source components, as well as the security and integrity of key software development processes. The results point to the fact that software supply chain security is still in its infancy.

Supply chain security is no easy task, and no single entity has end-to-end control. One company, stage, or process with insufficient security makes the entire chain more vulnerable to hackers and can open up a huge amount of risk when we consider the size and value of global chains that span many countries.