Security News

Microsoft disclosed on Jan. 19 that a nation-state backed attack occurred beginning in November 2023 in which the Russian state-sponsored threat actor group Midnight Blizzard accessed some Microsoft corporate emails and documents through compromised email accounts. The attackers gained access in November 2023 using a legacy test tenant account.

Updated The offensive cyber unit linked to Russia's Foreign Intelligence Service is exploiting the critical vulnerability affecting the JetBrains TeamCity CI/CD server at scale, and has been since September, authorities warn. The exploit in TeamCity could give attackers enough access to manipulate a software's source code, sign certificates, and compile and deploy processes, the advisory says.
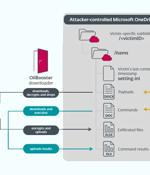
The Iranian state-sponsored threat actor known as OilRig deployed three different downloader malware throughout 2022 to maintain persistent access to victim organizations located in Israel. The...

Indian politicians and media figures have reported that Apple has warned them their accounts may be under attack by state-sponsored actors. Mahua's post therefore accuses India's government of being the state actor Apple believe has attacked her iPhone.

A number of government-backed APTs are exploiting CVE-2023-38831, a file extension spoofing vulnerability in WinRAR, a widely used file archiver utility for Windows. "The widespread exploitation of the WinRAR bug highlights that exploits for known vulnerabilities can be highly effective, despite a patch being available," Google TAG analysts have noted.
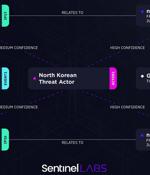
An analysis of the indicators of compromise associated with the JumpCloud hack has uncovered evidence pointing to the involvement of North Korean state-sponsored groups, in a style that's reminiscent of the supply chain attack targeting 3CX. The findings come from SentinelOne, which mapped out the infrastructure pertaining to the intrusion to uncover underlying patterns. "The North Korean threat actors demonstrate a high level of creativity and strategic awareness in their targeting strategies," SentinelOne security researcher Tom Hegel told The Hacker News.

Microsoft on Wednesday took the lid off a "Novel and distinct Russian threat actor," which it said is linked to the General Staff Main Intelligence Directorate and has a "Relatively low success rate." The tech giant's Threat Intelligence team, which was previously tracking the group under its emerging moniker DEV-0586, has graduated it to a named actor dubbed Cadet Blizzard.

A change in the deployment of the RomCom malware strain has illustrated the blurring distinction between cyberattacks motivated by money and those fueled by geopolitics, in this case Russia's illegal invasion of Ukraine, according to Trend Micro analysts. The infosec vendor pointed out that RomCom's operators, threat group Void Rabisu, also has links to the notorious Cuba ransomware, and therefore assessed it was assumed to be a financially driven criminal organization.

The threat actor uses a custom implant to compromise a specific TP-Link router model and steal information from it, as well as provide backdoor access to the attackers. "Horse Shell" implant found in TP-Link router firmware.

A Chinese state-sponsored APT group implanted malicious firmware into TP-Link routers as part of attack campaigns aimed at European foreign affairs entities, say Check Point researchers. The malicious firmware was exclusively created for TP-Link routers.