Security News
An active financially motivated campaign is targeting vulnerable SSH servers to covertly ensnare them into a proxy network. "This is an active campaign in which the attacker leverages SSH for remote access, running malicious scripts that stealthily enlist victim servers into a peer-to-peer proxy network, such as Peer2Profit or Honeygain," Akamai researcher Allen West said in a Thursday report.

Pub The command will print out your SSH key on your Linux machine without prompting you for your key authentication password. How to view your SSH public key on macOS. Viewing your keys on macOS can be done in a similar fashion as on Linux.

An unknown threat actor is brute-forcing Linux SSH servers to install a wide range of malware, including the Tsunami DDoS bot, ShellBot, log cleaners, privilege escalation tools, and an XMRig coin miner. Network administrators typically use SSH to manage Linux devices remotely, performing tasks such as running commands, changing the configuration, updating software, and troubleshooting problems.

Poorly managed Linux SSH servers are getting compromised by unknown attackers and instructed to engage in DDoS attacks while simultaneously mining cryptocurrency in the background. "The source code of Tsunami is publicly available so it is used by a multitude of threat actors. Among its various uses, it is mostly used in attacks against IoT devices. Of course, it is also consistently used to target Linux servers," researchers with AhnLab's Security Emergency response Center explained.

An updated version of the commodity malware called Legion comes with expanded features to compromise SSH servers and Amazon Web Services credentials associated with DynamoDB and CloudWatch. "This recent update demonstrates a widening of scope, with new capabilities such the ability to compromise SSH servers and retrieve additional AWS-specific credentials from Laravel web applications," Cado Labs researcher Matt Muir said in a report shared with The Hacker News.

Github has updated its SSH keys after accidentally publishing the private part to the world. A post on Github's security blog reveals that the company has changed its RSA SSH host keys.

Cloud-based repository hosting service GitHub said it took the step of replacing its RSA SSH host key used to secure Git operations "Out of an abundance of caution" after it was briefly exposed in a public repository. The activity, which was carried out at 05:00 UTC on March 24, 2023, is said to have been undertaken as a measure to prevent any bad actor from impersonating the service or eavesdropping on users' operations over SSH. "This key does not grant access to GitHub's infrastructure or customer data," Mike Hanley, chief security officer and SVP of engineering at GitHub, said in a post.

GitHub has rotated its private SSH key for GitHub.com after the secret was was accidentally published in a public GitHub repository. In a succinct blog post published today, GitHub acknowledged discovering this week that the RSA SSH private key for GitHub.com had been ephemerally exposed in a public GitHub repository.

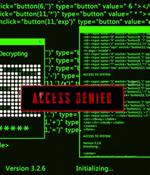
North Korean hackers are using trojanized versions of the PuTTY SSH client to deploy backdoors on targets' devices as part of a fake Amazon job assessment. A novel element in this campaign is the use of a trojanized version of the PuTTY and KiTTY SSH utility to deploy a backdoor, which in this case, is 'AIRDRY.V2'.
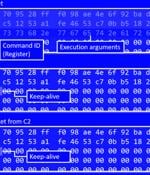
"This family borrows heavily from the original Mirai source code, but what separates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented in Mirai," Fortinet FortiGuard Labs said in a report. The malware, which gets its name from an embedded URL to a YouTube rap music video in an earlier version, is said to have amassed a growing collection of compromised SSH servers, with over 3,500 unique IP addresses used to scan and brute-force their way into the servers.