Security News

An international law enforcement operation involving 11 countries has disrupted the spreading of the FluBot Android malware, which spreads via SMS and MMS and steals sensitive information - passwords, online banking details, etc. The Dutch Police, who took control of the malware's infrastructure earlier in May, made the malware inactive.

An emailed report seemingly about a payment will, when opened in Excel on a Windows system, attempt to inject three pieces of file-less malware that steal sensitive information. From there, the malicious code will not only steal information, but can also remotely control aspects of the PC. The first of the three pieces of malware is AveMariaRAT, followed by Pandora hVCN RAT and BitRAT. AveMariaRAT has a range of features, from stealing sensitive data to achieving privilege escalation, remote desktop control, and camera capturing.

Spyware vendor Cytrox sold zero-day exploits to government-backed snoops who used them to deploy the firm's Predator spyware in at least three campaigns in 2021, according to Google's Threat Analysis Group. Based on CitizenLab's analysis of Predator spyware, Google's bug hunters believe that the buyers of these exploits operate in Egypt, Armenia, Greece, Madagascar, Côte d'Ivoire, Serbia, Spain, Indonesia, and possibly other countries.

In these attacks, part of three campaigns that started between August and October 2021, the attackers used zero-day exploits targeting Chrome and the Android OS to install Predator spyware implants on fully up-to-date Android devices. The government-backed malicious actors who purchased and used these exploits to infect Android targets with spyware are from Egypt, Armenia, Greece, Madagascar, Côte d'Ivoire, Serbia, Spain, and Indonesia, according to Google's analysis.

Google's Threat Analysis Group on Thursday pointed fingers at a North Macedonian spyware developer named Cytrox for developing exploits against five zero-day flaws, four in Chrome and one in Android, to target Android users. "The 0-day exploits were used alongside n-day exploits as the developers took advantage of the time difference between when some critical bugs were patched but not flagged as security issues and when these patches were fully deployed across the Android ecosystem," TAG researchers Clement Lecigne and Christian Resell said.

Spain's prime minister and defense minister are the latest elected officials to detect Pegasus spyware on their mobile phones, according to multiple media reports quoting Spanish authorities. During a press conference on Monday, Félix Bolaños, the minister for the presidency, told reporters that cellphones of Spanish prime minister Pedro Sánchez and defense minister Margarita Robles were both infected by NSO's notorious surveillance software last year.
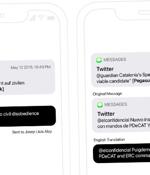
A previously unknown zero-click exploit in Apple's iMessage was used to install mercenary spyware from NSO Group and Candiru against at least 65 individuals as part of a "Multi-year clandestine operation." The attacks involved the weaponization of an iOS exploit dubbed HOMAGE that made it possible to penetrate the devices running versions prior to iOS 13.2, which was released on October 28, 2019.

An unknown zero-click exploit in Apple's iMessage was used by Israeli-based NSO Group to plant either Pegasus or Candiru malware on iPhones owned by politicians, journalists and activists. Citizen Lab, in collaboration with Catalan-based researchers, released the finding in a report on Monday that claims 65 people were targeted or infected with malware via an iPhone vulnerability called HOMAGE. It asserts the controversial Israeli firm the NSO Group and a second firm Candiru were behind the campaigns that took place between 2017 and 2020.

The Canadian research outfit also said it had identified at least 65 individuals linked with Catalan civil society groups in Spain who were targeted by, or infected with, surveillance software. On Monday, Citizen Lab, a part of at the University of Toronto's Munk School, said it had found likely NSO Group Pegasus spyware infections on devices associated with UK Prime Minister Boris Johnson's office, 10 Downing Street, and on devices linked to the FCO, now called the FCDO, or the Foreign Commonwealth and Development office.

Digital threat researchers at Citizen Lab have discovered a new zero-click iMessage exploit used to install NSO Group spyware on iPhones belonging to Catalan politicians, journalists, and activists. "Among Catalan targets, we did not see any instances of the HOMAGE exploit used against a device running a version of iOS greater than 13.1.3. It is possible that the exploit was fixed in iOS 13.2," Citizen Lab said.