Security News

Israeli Android users are targeted by a malicious version of the 'RedAlert - Rocket Alerts' app that, while it offers the promised functionality, acts as spyware in the background. RedAlert - Rocket Alerts is a legitimate open-source app used by Israeli citizens to receive notifications of incoming rockets targeting the country.

New findings have identified connections between an Android spyware called DragonEgg and another sophisticated modular iOS surveillanceware tool named LightSpy. DragonEgg, alongside WyrmSpy (aka...
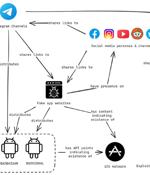
Tibetan, Uyghur, and Taiwanese individuals and organizations are the targets of a persistent campaign orchestrated by a threat actor codenamed EvilBamboo to gather sensitive information. "The...
The three zero-day flaws addressed by Apple on September 21, 2023, were leveraged as part of an iPhone exploit chain in an attempt to deliver a spyware strain called Predator targeting former...

Apple has emitted patches this week to close security holes that have been exploited in the wild by commercial spyware. We've just learned today that the Predator spyware sold by Intellexa used these vulnerabilities to infect at least one target's iPhone.

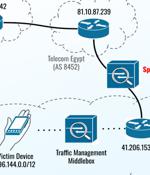
Security researchers with The Citizen Lab and Google's Threat Analysis Group revealed today that three zero-days patched by Apple on Thursday were abused as part of an exploit chain to install Cytrox's Predator spyware. Google TAG also observed the attackers using a separate exploit chain to drop Predator spyware on Android devices in Egypt, exploiting CVE-2023-4762-a Chrome bug patched on September 5th-as a zero-day to gain remote code execution.

Israeli software maker Insanet has reportedly developed a commercial product called Sherlock that can infect devices via online adverts to snoop on targets and collect data about them for the biz's clients. "Insanet is an Israeli company, which operates with full and absolute obligation to Israeli law and to its strict regulatory directives," the biz reportedly told the newspaper.

The iPhone belonging to Galina Timchenko, a prominent Russian journalist and critic of the government, was compromised with NSO Group's Pegasus spyware, a new collaborative investigation from Access Now and the Citizen Lab has revealed. The Washington Post reported that the Russian government is not a client of NSO Group, citing an unnamed person familiar with the company's operations.

The U.S. Cybersecurity and Infrastructure Security Agency ordered federal agencies today to patch security vulnerabilities abused as part of a zero-click iMessage exploit chain to infect iPhones with NSO Group's Pegasus spyware. On Monday, CISA added the two security flaws to its Known Exploited Vulnerabilities catalog, tagging them as "Frequent attack vectors for malicious cyber actors" and posing "Significant risks to the federal enterprise."

At the time the researchers published their report, several malicious apps were still available for download through Google Play. The Telegram apps presented in Kaspersky's report are promoted as "Faster" alternatives to the regular app.