Security News

Cybersecurity companies Mimecast and Qualys have apparently been targeted by the threat actor that breached the systems of IT management solutions provider SolarWinds as part of a sophisticated supply chain attack. Some experts believed at the time that the incident may be related to the SolarWinds breach, and Mimecast on Tuesday confirmed that the theft of the certificate was indeed related to the SolarWinds software compromise and carried out by the same hackers.

Email security company Mimecast has confirmed today that the threat actor behind the SolarWinds supply-chain attack is behind the security breach it disclosed earlier this month. "Our investigation has now confirmed that this incident is related to the SolarWinds Orion software compromise and was perpetrated by the same sophisticated threat actor," Mimecast said.

The British government has denied being "Complacent" over the Solarwinds hack as a fed-up peer of the realm urged a minister to "Answer the question". Lord True, the government's Cabinet Office spokesman in the House of Lords, described the attack as "a complex and global cyber incident" and said UK.gov was "Working with international partners to fully understand its scale and any UK impact."

Just days into his leadership role, U.S. President Joe Biden has instructed U.S. intelligence agencies to provide him with a detailed assessment of the SolarWinds hack, which fueled a global cyber espionage campaign impacting many high-profile government agencies and businesses. The U.S. government and others have said Russia is likely behind the highly sophisticated attack on SolarWinds.
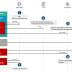
Microsoft on Wednesday shared more specifics about the tactics, techniques, and procedures adopted by the attackers behind the SolarWinds hack to stay under the radar and avoid detection, as cybersecurity companies work towards getting a "Clearer picture" of one of the most sophisticated attacks in recent history. "The attackers behind Solorigate are skilled campaign operators who carefully planned and executed the attack, remaining elusive while maintaining persistence," researchers from Microsoft 365 Defender Research Team, Microsoft Threat Intelligence Center, and Microsoft Cyber Defense Operations Center said.

Specifically, the compromised DLL file was quietly deployed onto targeted systems by mimicking legitimate file names - and the attackers worked between 8am and 5pm to increase the odds of not being spotted. Much of the infosec commentary around the SolarWinds supply chain attack has reused the tired old clichés of stating the attackers were sophisticated, advanced, cunning, soft, strong, thoroughly absorbent, and so on.

Microsoft on Wednesday released another report detailing the activities and the methods of the threat actor behind the attack on IT management solutions firm SolarWinds, including their malware delivery methods, anti-forensic behavior, and operational security. In its latest report on the SolarWinds attack, which it tracks as Solorigate, Microsoft explains how the attackers got from the Sunburst malware to the Cobalt Strike loaders, and how they kept the components separated as much as possible to avoid being detected.

Malwarebytes is the latest discovered victim of the SolarWinds hackers, the security company said - except that it wasn't targeted through the SolarWinds platform. "While Malwarebytes does not use SolarWinds, we, like many other companies were recently targeted by the same threat actor," it disclosed in a Tuesday web posting.

Microsoft today shared details on how the SolarWinds hackers were able to remain undetected by hiding their malicious activity inside the networks of breached companies. This previously unknown information was disclosed by security experts part of the Microsoft 365 Defender Research Team, Microsoft Threat Intelligence Center, and Microsoft Cyber Defense Operations Center.

Security company Malwarebytes suspects a breach of its Office 365 and Azure tenancies is by the same attacker behind the SolarWinds hack, but reckons flaws in Azure Active Directory security are also to blame. Malwarebytes, whose products include widely used anti-malware tools for consumers and businesses, said that it does not use SolarWinds but believes that the same attacker used "Another intrusion vector that works by abusing applications with privileged access to Microsoft Office 365 and Azure environments".