Security News

Apache Software has quickly issued a fix for a zero-day security bug in the Apache HTTP Server, which was first reported to the project last week. Path traversal issues allow unauthorized people to access files on a web server, by tricking either the web server or the web application running on it into returning files that exist outside of the web root folder.

The Telegraph newspaper managed to leak 10TB of subscriber data and server logs after leaving an Elasticsearch cluster unsecured for most of September, according to the researcher who found it online. After sampling the database to determine its owner, Diachenko saw the personal details of at least 1,200 Telegraph subscribers along with a substantial quantity of internal server logs, he told The Register.

Operators of an unknown ransomware gang are using a Python script to encrypt virtual machines hosted on VMware ESXi servers. While the Python programming language is not commonly used in ransomware development, it is a logical choice for ESXi systems, seeing that such Linux-based servers come with Python installed by default.

While investigating a misconfiguration flaw in Apache Airflow, researchers discovered many exposed instances over the web leaking sensitive information, including credentials, from well-known tech companies. Apache Airflow is a popular open-source workflow management platform for organizing and managing tasks.

Atom Silo, a newly spotted ransomware group, is targeting a recently patched and actively exploited Confluence Server and Data Center vulnerability to deploy their ransomware payloads. Ransomware gangs start targeting Confluence servers.

The latest version of the long-term support release of Windows Server, Windows Server 2022, is now available. Windows Server 2022 is the new long-term servicing channel release of Windows Server for on-premises data centers and virtual machines.

Researchers from the Microsoft Threat Intelligence Center have observed the APT it calls Nobelium using a post-exploitation backdoor dubbed FoggyWeb, to attack Active Directory Federation Services servers. Once a server is compromised, the threat group deploys FoggyWeb "To remotely exfiltrate the configuration database of compromised AD FS servers, decrypted token-signing certificates and token-decryption certificates," he said, which can be used to penetrate into users' cloud accounts.
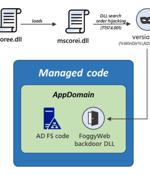
Microsoft on Monday revealed new malware deployed by the hacking group behind the SolarWinds supply chain attack last December to deliver additional payloads and steal sensitive information from Active Directory Federation Services servers. "Once Nobelium obtains credentials and successfully compromises a server, the actor relies on that access to maintain persistence and deepen its infiltration using sophisticated malware and tools," MSTIC researchers said.

The global server market size is expected to reach $145.31 billion by 2028, according to ResearchAndMarkets. Such developments are expected to cause an increase in the average selling prices of servers, which is expected to subsequently benefit the market growth.

VMware has released a security update that includes patches for 19 CVE-numbered vulnerabilities that affect the company's vCenter Server virtualization management platform and its hybrid Cloud Foundation platform for managing VMs and orchestrating containers. "This vulnerability can be used by anyone who can reach vCenter Server over the network to gain access, regardless of the configuration settings of vCenter Server," said Bob Plankers, Technical Marketing Architect at VMware.