Security News

European and U.S. law enforcement agencies have announced the dismantling of a bulletproof hosting service provider called Lolek Hosted, which cybercriminals have used to launch cyber-attacks...

The hacking of the UK's Electoral Commission was potentially facilitated by the exploitation of a vulnerability in Microsoft Exchange, according to a security expert. Earlier this week, the election oversight body disclosed that its systems had been broken into, and the attackers had access to the servers that host the organization's email, as well as copies of the electoral registers for the entire UK. It appears the Electoral Commission was running Microsoft Exchange Server with Outlook Web App facing the internet, and was vulnerable to an exploit known as ProxyNotShell at the time that suspicious activity was first detected on the Commission's systems in October 2022.
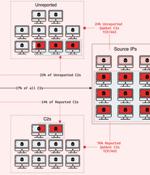
The operators associated with the QakBot malware have set up 15 new command-and-control servers as of late June 2023. The findings are a continuation of the malware's infrastructure analysis from Team Cymru, and arrive a little over two months after Lumen Black Lotus Labs revealed that 25% of its C2 servers are only active for a single day.
Vulnerable Redis services have been targeted by a "New, improved, dangerous" variant of a malware called SkidMap that's engineered to target a wide range of Linux distributions. "The malicious nature of this malware is to adapt to the system on which it is executed," Trustwave security researcher Radoslaw Zdonczyk said in an analysis published last week.

PaperCut recently fixed a critical security vulnerability in its NG/MF print management software that allows unauthenticated attackers to gain remote code execution on unpatched Windows servers. While it only impacts servers in non-default configurations where the external device integration setting is toggled, Horizon3 said in a report published on Friday that most Windows PaperCut servers have it enabled.

Hundreds of Citrix NetScaler ADC and Gateway servers have been breached by malicious actors to deploy web shells, according to the Shadowserver Foundation. The non-profit said the attacks take advantage of CVE-2023-3519, a critical code injection vulnerability that could lead to unauthenticated remote code execution.

Hundreds of Citrix Netscaler ADC and Gateway servers have already been breached and backdoored in a series of attacks targeting a critical remote code execution (RCE) vulnerability tracked as...

Threat actors are actively targeting exposed instances of SSH and Redis Redis open-source data store with a peer-to-peer self-replicating worm with versions for both Windows and Linux that the malware authors named P2Pinfect. After compromising a vulnerable Redis instance with an initial payload, P2PInfect downloads new OS-specific scripts and malicious binaries and adds the server to its list of infected systems.

Hackers are actively exploiting a 'BleedingPipe' remote code execution vulnerability in Minecraft mods to run malicious commands on servers and clients, allowing them to take control of the devices. BleedingPipe is a vulnerability found in many Minecraft mods caused by the incorrect use of deserialization in the 'ObjectInputStream' class in Java to exchange network packets between servers and clients.
The P2PInfect peer-to-peer worm has been observed employing previously undocumented initial access methods to breach susceptible Redis servers and rope them into a botnet. "The malware compromises exposed instances of the Redis data store by exploiting the replication feature," Cado Security researchers Nate Bill and Matt Muir said in a report shared with The Hacker News.