Security News

Authelia is an open-source authentication and authorization server that offers 2FA and SSO for applications through a web portal. Authelia connects directly to the reverse proxy but never to the application backends.

GitHub has rolled out fixes to address a maximum severity flaw in the GitHub Enterprise Server (GHES) that could allow an attacker to bypass authentication protections. Tracked...

GitHub has fixed a maximum severity (CVSS v4 score: 10.0) authentication bypass vulnerability tracked as CVE-2024-4986, which impacts GitHub Enterprise Server (GHES) instances using SAML single...

Microsoft has acknowledged a new known issue causing this month's KB5037765 security update for Windows Server 2019 to fail to install with 0x800f0982 errors. This confirmation comes after many Windows admins reported seeing install failures when trying to deploy cumulative updates released during the May 2024 Patch Tuesday on Windows Server 2019 systems.

In many cases, Ebury operators could gain full access to large servers of ISPs and well-known hosting providers. "We have documented cases where the infrastructure of hosting providers was compromised by Ebury. In these cases, we have seen Ebury being deployed on servers rented out by those providers, with no warning to the lessees. This resulted in cases where the Ebury actors were able to compromise thousands of servers at once," says Marc-Etienne M. Léveillé, the ESET researcher who investigated Ebury for more than a decade.
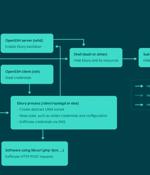
A malware botnet called Ebury is estimated to have compromised 400,000 Linux servers since 2009, out of which more than 100,000 were still compromised as of late 2023. The findings come from...

Microsoft has fixed a known issue causing NTLM authentication failures and domain controller reboots after installing last month's Windows Server security updates. [...]

A malware botnet known as 'Ebury' has infected almost 400,000 Linux servers since 2009, with roughly 100,000 still compromised as of late 2023. "While 400,000 is a massive number, it's important to mention that this is the number of compromises over the course of almost 15 years. Not all of those machines were compromised at the same time," explains ESET. "There is a constant churn of new servers being compromised while others are being cleaned up or decommissioned. The data at our disposal doesn't indicate when the attackers lost access to the systems, so it's difficult to know the size of the botnet at any specific point in time."

Microsoft has confirmed that last month's Windows Server security updates may also cause domain controller reboots after the Local Security Authority Subsystem Service process crashes. "In rare instances, Windows Servers running the Domain Controller role might experience Local Security Authority Subsystem Service crashes resulting in a reboot," Microsoft explains in a new update added to the Windows release health dashboard.

"TunnelVision's effect is independent of the underlying VPN protocol because it reconfigures the operating system network stack the VPN relies on." Anyone who is able to operate a DHCP server on the same network as someone using a VPN, and get that VPN client's machine to use that DHCP server, can decloak their traffic because of a particular feature in the configuration protocol: option 121, which allows administrators to add classless static routes to client routing tables.