Security News

Security breaches could have catastrophic consequences for any business, from costly downtime to exposure of customer data that could result in fines and lawsuits. Now you can get lifetime access to one of the most comprehensive high-quality bundles of security training courses ever seen on the market, The Complete 2023 Cyber Security Developer & IT Skills Bundle.
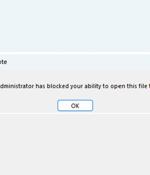
Microsoft has announced plans to automatically block embedded files with "Dangerous extensions" in OneNote following reports that the note-taking service is being increasingly abused for malware delivery. Microsoft said it intends to prevent users from directly opening an embedded file with a dangerous extension and display the message: "Your administrator has blocked your ability to open this file type in OneNote."

68% of data security professionals have identified shadow data as their top concern when it comes to protecting cloud data. While security teams are confident that they have complete visibility into new public cloud data repositories, 93% are concerned about shadow data, up 11% from the year before, and 68% of respondents say it is the greatest challenge in protecting cloud data.

To strengthen their cybersecurity posture, companies must spend valuable resources on maintaining or updating systems, hiring and training staff, and implementing security software - resources and options that many don't have readily available. For businesses, security breaches risk not only exposure to customer data and a decrease in trust, but also losses in revenue if systems are taken offline through attacks such as DDoS. "The findings in this report show that SMBs have specific needs and pain points, particularly when it comes to hiring and having dedicated security employees," said Tyler Healy, VP of Security at DigitalOcean.

Capita - everyone's favorite outsourcing badass - is still working to restore services for some customers after admitting the IT outage of certain services on Friday was caused by a cyber attack and efforts to contain the spread. The shape shifting tech biz, which has £6.5 billion worth of public sector contracts booked in, said before the weekend that a technical problem meant staff couldn't access work IT, including Microsoft cloud accounts. The cause of that blackout was confirmed today, with Capita saying via its website that on March 31 the biz "Experienced a cyber incident primarily impacting access to internal Microsoft 365 applications. This caused disruption to some services provided to individual clients, though the majority of our client services remained in operation."

Data storage devices maker Western Digital on Monday disclosed a "Network security incident" that involved unauthorized access to its systems.The breach is said to have occurred on March 26, 2023, enabling an unnamed third party to gain access to a "Number of the company's systems."

US-based data storage company Western Digital has announced that it has suffered a network security incident that resulted in an unauthorized third party gaining access to a number of the company's systems and some company data. Western Digital identified the network security incident on March 26, 2023.
In this Help Net Security interview, Kevin Muller, CEO at Passbolt, delves into the critical concerns linked to password usage, outlines how the Passbolt password manager guarantees the utmost level of security for businesses, highlights its features in the competitive landscape, sheds light on how Passbolt meets the distinct requirements of teams and organizations, and more. Passbolt is developed using proven security standards like OpenPGP and complies with security auditing standards such as SOC2 Type II. All of our security practices meet or exceed industry standards.

Given the importance of the Treasury department's function to Britain, Reg readers might expect the Head of Cyber Security vacancy currently being advertised would come with a salary that reflects its criticality. "We're looking for a Head of Cyber Security to join the team and provide advice to seniors on cyber risks across our services and systems," the posting reads.

In this Help Net Security interview, Michal Cizek, CEO at GoodAccess, discusses the crucial balance between leveraging distributed resources and maintaining top-notch security measures. Implementing zero-trust security often means redesigning the access policy from the start.