Security News
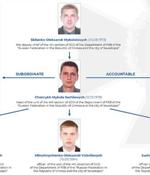
Ukraine's premier law enforcement and counterintelligence agency on Thursday disclosed the real identities of five individuals allegedly involved in digital intrusions attributed to a cyber-espionage group named Gamaredon, linking the members to Russia's Federal Security Service. Calling the hacker group "An FSB special project, which specifically targeted Ukraine," the Security Service of Ukraine said the perpetrators "Are officers of the 'Crimean' FSB and traitors who defected to the enemy during the occupation of the peninsula in 2014.".
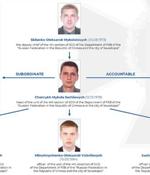
Ukraine's premier law enforcement and counterintelligence agency on Thursday disclosed the real identities of five individuals allegedly involved in cyberattacks attributed to a cyber-espionage group named Gamaredon, linking the members to Russia's Federal Security Service. Calling the hacker group "An FSB special project, which specifically targeted Ukraine," the Security Service of Ukraine said the perpetrators "Are officers of the 'Crimean' FSB and traitors who defected to the enemy during the occupation of the peninsula in 2014.".

SSU and the Ukrainian secret service say they have identified five members of the Gamaredon hacking group, a Russian state-sponsored operation known for targeting Ukraine since 2014. This Gamaredon hacking group, tracked as Armageddon by the SSU, is allegedly operated under the FSB and is believed to be responsible for over 5,000 attacks in Ukraine since the operation began.

A Russian national, who was arrested in South Korea last month and extradited to the U.S. on October 20, appeared in a federal court in the state of Ohio on Thursday to face charges for his alleged role as a member of the infamous TrickBot group. Starting its roots as a banking trojan in 2016, TrickBot has evolved into a modular, multi-stage Windows-based crimeware solution capable of pilfering valuable personal and financial information, and even dropping ransomware and post-exploitation toolkits on compromised devices.

The US Department of Justice claims it's arrested a member of a gang that deployed the Trickbot ransomware. A heavily-redacted indictment names Vladimir Dunaev as a developer of the malware, and alleges he was "a Malware Developer for the Trickbot Group, overseeing the creation of internet browser injection, machine identification, and data harvesting codes used by the Trickbot malware".

Nobelium has been attempting to replicate the approach it has used in past attacks by targeting organizations integral to the global IT supply chain. This time, it is attacking a different part of the supply chain: resellers and other technology service providers that customize, deploy and manage cloud services and other technologies on behalf of their customers.

The Grief ransomware gang claims to have attacked the National Rifle Association and released stolen data as proof of the attack. Today, the ransomware gang added the NRA as a new victim on their data leak site while displaying screenshots of Excel spreadsheets containing US tax information and investments amounts.

The cybercrime group behind the SolarWinds hack remains focused on the global IT supply chain, says Microsoft, with 140 resellers and service providers targeted since May. The Russian-backed hacking group responsible for the SolarWinds attack has been targeting more companies with the goal of disrupting the worldwide IT supply chain.In a blog post published Monday, Microsoft cautioned of new attacks by Nobelium, revealing that it notified 140 resellers and technology service providers targeted by the group.

The Ukrainian cybercrime police force has arrested members of a group of money launderers and hackers at the request of U.S. intelligence services. In a press release by Ukraine's SSU, law enforcement says the individuals engaged in large-scale international operations where they laundered tens of millions of USD for various hacking groups.

A report analyzing data from the start of the year concludes that distributed denial-of-service attacks on Russian companies have increased 2.5 times compared to the same period last year. DDoS attacks are commonly used to extort victims with ransom demands or as a distraction for IT teams while hackers attempt to steal precious data from compromised systems.