Security News

A collection of 21 security flaws have been discovered in Sierra Wireless AirLink cellular routers and open-source software components like TinyXML and OpenNDS. Collectively tracked as Sierra:21,...

Forescout detailed the discovery of 21 new vulnerabilities in OT/IoT routers and open-source software elements. The "SIERRA:21 - Living on the Edge" report features research into Sierra Wireless AirLink cellular routers and some open-source components, such as TinyXML and OpenNDS. Sierra Wireless routers are popular - an open database of Wi-Fi networks shows 245,000 networks worldwide running Sierra Wireless for various applications.

A set of 21 newly discovered vulnerabilities impact Sierra OT/IoT routers and threaten critical infrastructure with remote code execution, unauthorized access, cross-site scripting, authentication bypass, and denial of service attacks. The flaws discovered by Forescout Vedere Labs affect Sierra Wireless AirLink cellular routers and open-source components like TinyXML and OpenNDS. AirLink routers are highly regarded in the field of industrial and mission-critical applications due to high-performance 3G/4G/5G and WiFi and multi-network connectivity.

Cybersecurity researchers have discovered a new variant of an emerging botnet called P2PInfect that's capable of targeting routers and IoT devices. The latest version, per Cado Security Labs, is...

An active malware campaign is leveraging two zero-day vulnerabilities with remote code execution (RCE) functionality to rope routers and video recorders into a Mirai-based distributed...

Akamai has uncovered two zero-day bugs capable of remote code execution, both being exploited to distribute the Mirai malware and built a botnet army for distributed denial of service attacks. Because the security holes aren't plugged yet, Akamai's Security Intelligence Response Team did not name the brands or the affected devices.

A new Mirai-based malware botnet named 'InfectedSlurs' has been exploiting two zero-day remote code execution vulnerabilities to infect routers and video recorder devices. The malware hijacks the devices to make them part of its DDoS swarm, presumably rented for profit.

Cisco Talos discovered a new critical zero-day vulnerability in the Web User Interface feature of Cisco IOS XE software that's currently being used in the wild. The vulnerability used to access the system and create those accounts is CVE-2023-20198; it received the highest Common Vulnerability Scoring System score of 10.
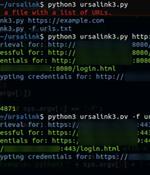
A severity flaw impacting industrial cellular routers from Milesight may have been actively exploited in real-world attacks, new findings from VulnCheck reveal. Tracked as CVE-2023-43261 (CVSS...

A Mirai-based DDoS malware botnet tracked as IZ1H9 has added thirteen new payloads to target Linux-based routers and routers from D-Link, Zyxel, TP-Link, TOTOLINK, and others. IZ1H9 compromises devices to enlist them to its DDoS swarm and then launches DDoS attacks on specified targets, presumably on the order of clients renting its firepower.