Security News

Cybersecurity researchers have unpacked a new Golang-based botnet called Kraken that's under active development and features an array of backdoor capabilities to siphon sensitive information from compromised Windows hosts. The botnet - not to be confused with a 2008 botnet of the same name - is perpetuated using SmokeLoader, which chiefly acts as a loader for next-stage malware, allowing it to quickly scale in size and expand its network.

"The DDoS attacks against the Ukrainian defense ministry and financial institutions appear to be harassment similar to the previous DDoS attacks seen in January," Rick Holland, CISO at Digital Shadows, said via email. In the past two months, Russian- advanced persistent threats have been tied to an attack on 70 Ukrainian government websites, a wiper targeting government, non-profit and IT organizations, and increased attacks and espionage against military targets.

Cybersecurity researchers have detailed the inner workings of ShadowPad, a sophisticated and modular backdoor that has been adopted by a growing number of Chinese threat groups in recent years, while also linking it to the country's civilian and military intelligence agencies. ShadowPad is a modular malware platform sharing noticeable overlaps to the PlugX malware and which has been put to use in high-profile attacks against NetSarang, CCleaner, and ASUS, causing the operators to shift tactics and update their defensive measures.
A researcher has demonstrated how he was able to successfully recover text that had been redacted using the pixelation technique. Further, the researcher has released a GitHub tool that can be used by anyone to reconstruct text from obscure, pixelated images.
A researcher has demonstrated how he was able to successfully recover text that had been redacted using the pixelation technique. Further, the researcher has released a GitHub tool that can be used by anyone to reconstruct text from obscure, pixelated images.

Researchers discover common threat actor behind aviation and defense malware campaigns. Security researchers at Proofpoint have announced their discovery of a common threat actor behind attacks reported by Cisco Talos, Microsoft and others, and they say that the group has been active since at least 2017.

A quantum gate between the ions can be implemented using electric fields. One is a so-called trapped-ion platform, one of the most promising candidates for quantum computing that makes use of ions - atoms that have either a surplus or a shortage of electrons and as a result are electrically charged.
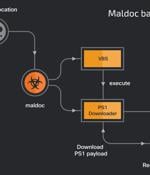
Details have emerged about a previously undocumented malware campaign undertaken by the Iranian MuddyWater advanced persistent threat group targeting Turkish private organizations and governmental institutions. "This campaign utilizes malicious PDFs, XLS files and Windows executables to deploy malicious PowerShell-based downloaders acting as initial footholds into the target's enterprise," Cisco Talos researchers Asheer Malhotra and Vitor Ventura said in a newly published report.

A group of academics at South Korea's Gwangju Institute of Science and Technology have utilized natural silk fibers from domesticated silkworms to build an environmentally friendly digital security system that they say is "Practically unbreachable." "The first natural physical unclonable function [] takes advantage of the diffraction of light through natural microholes in native silk to create a secure and unique digital key for future security solutions," the researchers said.

A team of researchers from French, Israeli, and Australian universities has explored the possibility of using people's GPUs to create unique fingerprints and use them for persistent web tracking. The researchers considered the possibility of creating distinctive fingerprints based on the GPU of the tracked systems with the help of WebGL. WebGL is a cross-platform API for rendering 3D graphics in the browser, and it's present on all modern web browsers.