Security News

Organizations are combating excessive remote access demands with an equally excessive number of tools that provide varying degrees of security, according to Claroty. Data from more than 50,000...
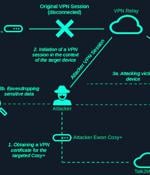
Security vulnerabilities have been disclosed in the industrial remote access solution Ewon Cosy+ that could be abused to gain root privileges to the devices and stage follow-on attacks. The elevated access could then be weaponized to decrypt encrypted firmware files and encrypted data such as passwords in configuration files, and even get correctly signed X.509 VPN certificates for foreign devices to take over their VPN sessions.

Researchers are warning of threat actors increasingly abusing the Cloudflare Tunnel service in malware campaigns that usually deliver remote access trojans (RATs). [...]

Geyer also addresses the challenges and solutions for securing remote access to critical OT assets. The trend of connecting previously isolated OT assets to public networks is driven by several factors, including the need for real-time data analysis, remote management, operational efficiency, and improved decision-making.

Attackers are trying to gain access to Check Point VPN devices via local accounts protected only by passwords, the company has warned on Monday. In mid-April 2024, Cisco Talos warned about a global increase in brute-force attacks against VPN services, web application authentication interfaces and SSH services.

As corporate conglomerates, small businesses and brick-and-mortar shops fade away in favor of a distributed offsite workforce, companies and employees can profit from the greater convenience and efficiency provided by remote access. Combined with a bring your own device policy, remote access can lower equipment costs, reduce office overhead and facilitate employee productivity.

The notorious North Korea-linked threat actor known as the Lazarus Group has been attributed to a new global campaign that involves the opportunistic exploitation of security flaws in Log4j to...

Cybercriminals still prefer targeting open remote access products, or like to leverage legitimate remote access tools to hide their malicious actions, according to WatchGuard. "Threat actors continue using different tools and methods in their attack campaigns, making it critical for organizations to keep abreast of the latest tactics to fortify their security strategy," said Corey Nachreiner, chief security officer at WatchGuard.

Security researchers are warning that hackers are targeting multiple healthcare organizations in the U.S. by abusing the ScreenConnect remote access tool. [...]

The Everest ransomware group is stepping up its efforts to purchase access to corporate networks directly from employees amid what researchers believe to be a major transition for the cybercriminals. Everest ransomware group's message on its deep web blog advertising its intent to recruit corporate insiders.