Security News
Gigabud RAT was first documented by Cyble in January 2023 after it was spotted impersonating bank and government apps to siphon sensitive data. While Android devices have the "Install from Unknown Sources" setting disabled by default as a security measure to prevent the installation of apps from untrusted sources, the operating system allows other apps on installed on the device, such as web browsers, email clients, file managers, and messaging apps, to request the "REQUEST INSTALL PACKAGES" permission.

Attackers can turn AWS SSM agents into remote access trojansMitiga researchers have documented a new post-exploitation technique attackers can use to gain persistent remote access to AWS Elastic Compute Cloud instances, as well as to non-EC2 machines. August 2023 Patch Tuesday forecast: Software security improvementsThe continued onslaught of phishing attacks, ransomware deployment, and other exploitation is forcing the community to pay closer attention to early identification, as well as fast response, to vulnerabilities in their software.

Abusing AWS SSM Agent as a RAT. AWS Systems Manager is an Amazon-signed binary and comprehensive endpoint management system used by administrators for configuration, patching, and monitoring AWS ecosystems comprising EC2 instances, on-premise servers, or virtual machines. Mitiga's discovery is that the SSM agent can be configured to run in "Hybrid" mode even from within the limits of an EC2 instance, allowing access to assets and servers from attacker-controlled AWS accounts.
Threat actors are creating fake websites hosting trojanized software installers to trick unsuspecting users into downloading a downloader malware called Fruity with the goal of installing remote trojans tools like Remcos RAT. "Among the software in question are various instruments for fine-tuning CPUs, graphic cards, and BIOS; PC hardware-monitoring tools; and some other apps," cybersecurity vendor Doctor Web said in an analysis. "Such installers are used as a decoy and contain not only the software potential victims are interested in, but also the trojan itself with all its components."

The threat actors behind the RomCom RAT have been suspected of phishing attacks targeting the upcoming NATO Summit in Vilnius as well as an identified organization supporting Ukraine abroad. The findings come from the BlackBerry Threat Research and Intelligence team, which found two malicious documents submitted from a Hungarian IP address on July 4, 2023. RomCom, also tracked under the names Tropical Scorpius, UNC2596, and Void Rabisu, was recently observed staging cyber attacks against politicians in Ukraine who are working closely with Western countries and a U.S.-based healthcare organization involved with aiding refugees fleeing the war-torn country.

A stealthy remote access trojan named 'SeroXen' has recently gained popularity as cybercriminals begin using it for its low detection rates and powerful capabilities. AT&T reports that the malware is sold under the guise of a legitimate remote access tool for Windows 11 and 10 for $15/month or a single "Lifetime" license payment of $60. While marketed as a legitimate program, the Flare Systems cyber intel platform has shown that SeroXen is promoted as a remote access trojan on hacking forums.

The threat actors behind RomCom RAT are leveraging a network of fake websites advertising rogue versions of popular software at least since July 2022 to infiltrate targets. The remote access trojan has since been used heavily in attacks targeting Ukrainian state bodies and military systems via spoofed versions of legitimate software.
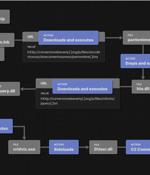
The suspected Pakistan-aligned threat actor known as SideCopy has been observed leveraging themes related to the Indian military research organization as part of an ongoing phishing campaign. Interestingly, the same attack chains have been observed to load and execute Action RAT as well as an open source remote access trojan known as AllaKore RAT. The latest infection sequence documented by Fortinet is no different, leading to the deployment of an unspecified strain of RAT that's capable of communicating with a remote server and launching additional payloads.
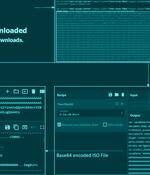
A new phishing campaign has set its sights on European entities to distribute Remcos RAT and Formbook via a malware loader dubbed DBatLoader. "The malware payload is distributed through WordPress websites that have authorized SSL certificates, which is a common tactic used by threat actors to evade detection engines," Zscaler researchers Meghraj Nandanwar and Satyam Singh said in a report published Monday.

Ukraine's cyberpolice has arrested the developer of a remote access trojan malware that infected over 10,000 computers while posing as game applications. "The man developed viral software, which he positioned as applications for computer games."