Security News
A suspected Chinese-speaking threat actor has been attributed to a malicious campaign that targets the Uzbekistan Ministry of Foreign Affairs and South Korean users with a remote access trojan...

Threat actors are targeting the education, government and business services sectors with a remote access trojan called NetSupport RAT. "The delivery mechanisms for the NetSupport RAT encompass...

Cybersecurity researchers have uncovered a new set of malicious packages published to the NuGet package manager using a lesser-known method for malware deployment. Software supply chain security...

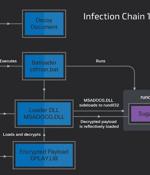
The open-source remote access trojan known as Quasar RAT has been observed leveraging DLL side-loading to fly under the radar and stealthily siphon data from compromised Windows hosts. "This...

Malicious NuGet packages appearing to have over 2 million downloads impersonate crypto wallets, crypto exchange, and Discord libraries to infect developers with the SeroXen remote access trojan. The malicious packages uploaded on NuGet by a user named 'Disti' were discovered by Phylum researchers, who published a report today to warn about the threat.

A malicious package hosted on the NuGet package manager for the .NET Framework has been found to deliver a remote access trojan called SeroXen RAT. The package, named...

Despite the disruption to its infrastructure, the threat actors behind the QakBot malware have been linked to an ongoing phishing campaign since early August 2023 that led to the delivery of...

Windows users looking to install the Bitwarden password manager may have inadvertently installed a remote access trojan. A malicious website spoofing Bitwarden's legitimate one has been offering fake installation packages containing the ZenRAT malware.

A malicious actor released a fake proof-of-concept (PoC) exploit for a recently disclosed WinRAR vulnerability on GitHub with an aim to infect users who downloaded the code with Venom RAT malware....
Chinese-language speakers have been increasingly targeted as part of multiple email phishing campaigns that aim to distribute various malware families such as Sainbox RAT, Purple Fox, and a new...