Security News

An open-source Android malware named 'Rafel RAT' is widely deployed by multiple cybercriminals to attack outdated devices, some aiming to lock them down with a ransomware module that demands payment on Telegram. Researchers Antonis Terefos and Bohdan Melnykov at Check Point report detecting over 120 campaigns using the Rafel RAT malware.

An open-source Android malware named 'Ratel RAT' is widely deployed by multiple cybercriminals to attack outdated devices, some aiming to lock them down with a ransomware module that demands payment on Telegram. This proves Ratel RAT is an effective attack tool against an array of different Android implementations.

A previously undocumented cross-platform malware codenamed Noodle RAT has been put to use by Chinese-speaking threat actors either for espionage or cybercrime for years. While this backdoor was...

Cybersecurity researchers have uncovered a new suspicious package uploaded to the npm package registry that's designed to drop a remote access trojan (RAT) on compromised systems. The package in...

The North Korea-linked threat actor known as Andariel has been observed using a new Golang-based backdoor called Dora RAT in its attacks targeting educational institutes, manufacturing firms, and...
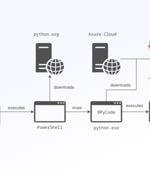
Brazilian banking institutions are the target of a new campaign that distributes a custom variant of the Windows-based AllaKore remote access trojan (RAT) called AllaSenha. The malware is...
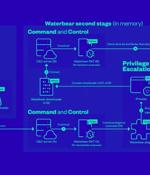
Interestingly, the RAT module is fetched twice from the attacker-controlled infrastructure, the first of which is just used to load the Waterbear plugin that subsequently launches a different version of the Waterbear downloader to retrieve the RAT module from another C&C server. Put differently, the first Waterbear RAT serves as a downloader while the second Waterbear RAT functions as a backdoor, harvesting sensitive information from the compromised host through a set of 60 commands.
The financially motivated threat actor known as FIN7 has been observed leveraging malicious Google ads spoofing legitimate brands as a means to deliver MSIX installers that culminate in the...

The North Korea-linked threat actor known as Lazarus Group employed its time-tested fabricated job lures to deliver a new remote access trojan called Kaolin RAT. The malware could, "aside from...

Two individuals have been arrested in Australia and the U.S. in connection with an alleged scheme to develop and distribute a remote access trojan called Hive RAT (previously Firebird). The U.S....