Security News

Good cyber and physical security can make or break companies. The purpose of this Security Response Policy, written by Scott Matteson for TechRepublic Premium, is to outline the security incident response processes which must be followed.

Customer information is usually one of the favorite targets of hackers as it contains confidential details which can be used to commit property or identity theft. Even innocent mistakes such as a lost mobile device that contains customer information can wreak havoc.

Risk management involves the practice of addressing and handling threats to the organization in the form of cybersecurity attacks and compromised or lost data. The process of establishing appropriate risk management guidelines is critical to ensure company operations and reputation do not suffer adverse impacts.

As corporate conglomerates, small businesses and brick-and-mortar shops fade away in favor of a distributed offsite workforce, companies and employees can profit from the greater convenience and efficiency provided by remote access. Combined with a bring your own device policy, remote access can lower equipment costs, reduce office overhead and facilitate employee productivity.

Every company's network is made up of devices that transmit and store information. To protect company data and reputation, it is essential to ensure that the network is secured from unauthorized access, data loss, malware infestations and security breaches.

69% consider this data storage essential to their corporate cybersecurity, and only 12% of those who deployed immutable data storage say it is not essential. This is followed by France at 96%, Germany at 94% and the UK at 85%. While a relatively low number of IT leaders worldwide who currently use immutable data storage do not regard it as "Essential" to their cybersecurity strategy, a larger percentage resides in the UK: 24% of UK respondents have deployed it but say it is not essential to their cybersecurity, compared to 11% in France, 9% in the US and 6% in Germany.

Any given technological environment is useless if its main purpose for existence - the processing and sharing of information - is threatened or eliminated. With that in mind, a sound policy on how to secure business information is essential for smooth company operations and ensuring a successful future.

While security principles should apply throughout the organization, locking down the perimeter and ensuring only necessary connections get through is an especially critical goal. Whether traffic is going from outside to inside or vice versa, having a strong, comprehensive and reliable perimeter security policy is integral to securing organizational data and the employees who use it to do their jobs and conduct company business.
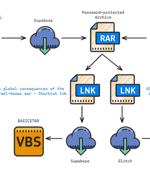
The Iranian-origin threat actor known as Charming Kitten has been linked to a new set of attacks aimed at Middle East policy experts with a new backdoor called BASICSTAR by creating a fake webinar...

This policy from TechRepublic Premium provides information on defining an incident, assigning an incident response team, documenting a plan and conducting a response. DOCUMENT AN INCIDENT RESPONSE PLAN. Draw up a plan for incident response and start by including a detailed list of system/application/device information.