Security News

The Hushed Private Phone Line lifetime subscription gives you a second phone line for calls and texts where you don't want to share your personal number. Hushed earned 4.6 stars out of five on the Apple App Store by being both easy to use and effective at protecting privacy.
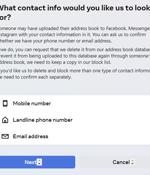
Facebook appears to have silently rolled out a tool that allows users to remove their contact information, such as phone numbers and email addresses, uploaded by others. When users sync the contact lists on their devices with Facebook, it's worth pointing out the privacy violation, which stems from the fact that those contacts didn't explicitly consent to the upload. "Someone may have uploaded their address book to Facebook, Messenger or Instagram with your contact information in it," Facebook notes in the page.

After a successful pilot program in Korea, Samsung is now rolling out 'Maintenance Mode' to select Galaxy devices globally, to help users protect their sensitive data when they hand over their smartphones at service points. "With Maintenance Mode, we are giving extra reassurance that Galaxy users can keep their privacy, even if they hand their phone to someone" - Samsung.

If adopted, these rules would - according to a top British computer security expert - authorize the reading and analysis of people's previously private communication for the sake of potentially preventing the spread of child sex abuse material and terrorism communications. In a paper titled Chat Control or Child Protection?, to be distributed via ArXiv, Anderson offers a rebuttal to arguments advanced in July by UK government cyber and intelligence experts Ian Levy, technical director of the UK National Cyber Security Centre, and Crispin Robinson, technical director of cryptanalysis at Government Communications Headquarters, the UK's equivalent to the NSA. That pro-snoop paper, penned by Levy and Robinson and titled Thoughts on Child Safety on Commodity Platforms, was referenced on Monday by EU Commissioner for Home Affairs, Ylva Johansson, before the European Parliament's Civil Liberties Committee in support of the EU Child Sexual Abuse Regulation, according to Anderson.

The Washington Post is reporting that the US Customs and Border Protection agency is seizing and copying cell phone, tablet, and computer data from "As many as" 10,000 phones per year, including an unspecified number of American citizens. This is done without a warrant, because "Courts have long granted an exception to border authorities, allowing them to search people's devices without a warrant or suspicion of a crime."

The Lorenz ransomware gang now uses a critical vulnerability in Mitel MiVoice VOIP appliances to breach enterprises, using their phone systems for initial access to their corporate networks. While these incidents weren't linked to a specific ransomware gang, Arctic Wold Labs was able to attribute similar malicious activity to the Lorenz gang with high confidence.

iPhone 14 cheat sheet: Everything to know about Apple's 2022 flagship phones We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. The iPhone 14 and iPhone 14 Plus feature an A15 Bionic chip comprising of a 5-core CPU that's 18% faster for gaming performance than the iPhone 13; a 6-core CPU with 2 high-performance cores and 4 high efficiency cores that produce more performance and increase battery life; and a new image signal processor that works with the new camera system to produce a better image handling pipeline.
The U.S. Federal Trade Commission on Monday said it filed a lawsuit against Kochava, a location data broker, for collecting and selling precise geolocation data gathered from consumers' mobile devices. The complaint alleges that the U.S. company amasses a "Wealth of information" about users by purchasing data from other data brokers to sell to its own clients.
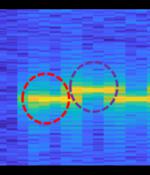
At around the same time that the Rhythm Nation story broke, a researcher at Ben-Gurion university of the Negev in Israel published a research paper about resonance problems in mobile phone gyroscopes, as used by popular but apparently innocent programs such as your Compass app. At the same time, a typical mobile phone microphone can pick up ultrasonic sounds at the other side of the airgap.

All users can rest assured that their message history, contact lists, profile information, whom they'd blocked, and other personal data remain private and secure and were not affected. For about 1,900 users, an attacker could have attempted to re-register their number to another device or learned that their number was registered to Signal.