Security News

The U.S. Financial Industry Regulatory Authority has issued a notice warning member brokerage firms of widespread phishing attacks using surveys to harvest information. FINRA is a non-profit organization and self-regulatory body authorized by the U.S. government to regulate exchange markets and brokerage firms.

David Mitchell, Senior Director of Email Product Management at Sophos, shares his top tips to optimize workplace email security. Five steps to secure your organization's email.

We do a show on Facebook every week in our Naked Security Live video series, where we discuss one of the big security concerns of the week. For those of you who [a] don't use Facebook, [b] had buffering problems while we were live, [c] would like subtitles, or [d] simply want to catch up later, we also upload the recorded videos to our YouTube channel.
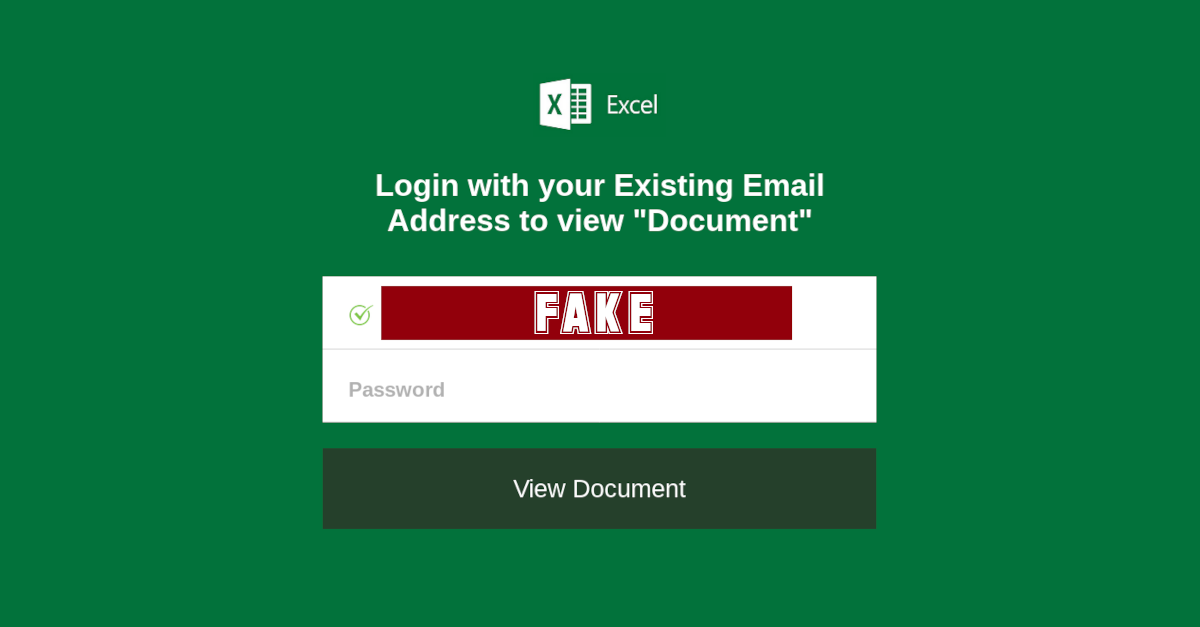
Or the imposter pages may be part of a short-lived web hosting account - perhaps set up just a day or two before as a "Free trial" that will probably be shut down quickly, but not before the crooks will have cut and run anyway. Usually, the fake login form that performs the password-stealing part of a phishing scam appears somewhere in the phoney web page on website.
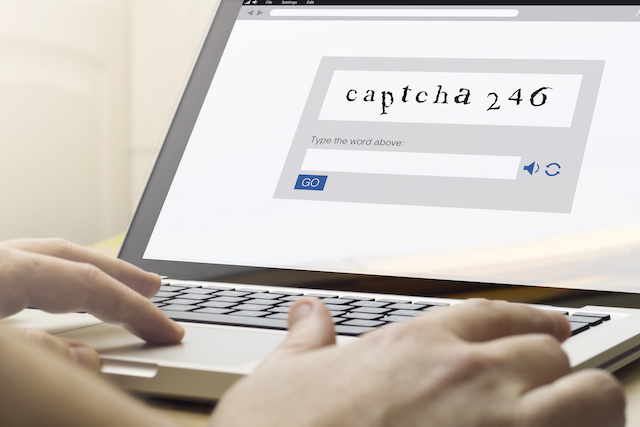
Researchers are warning of an ongoing Office 365 credential-phishing attack that's targeting the hospitality industry - and using visual CAPTCHAs to avoid detection and appear legitimate. Though the use of CAPTCHAS in phishing attacks is nothing groundbreaking, this attack shows that the technique works - so much so that the attackers in this campaign used three different CAPTCHA checks on targets, before finally bringing them to the phishing landing page, which poses as a Microsoft Office 365 log-in page.

According to researchers from Proofpoint, targets receive a well-crafted lures asking them to click a link which carries them to the legitimate Microsoft third-party apps consent page. "The ability to perform reconnaissance on an O365 account supplies an actor with valuable information that can later be weaponized in business email compromise attacks or account takeoversThe minimal [read-only] permissions requested by these apps also likely help them appear inconspicuous if an organization's O365 administrator audits connected apps for their users' accounts."

Washington state is among those being targeted by a "Large-scale, highly sophisticated" nationwide phishing campaign, the office of Gov. Jay Inslee said Thursday. At a press conference Thursday, Inslee said that the state is taking proactive measures to protect state systems, but he said that no ransomware activity has occurred among the agencies targeted, and no state services have been impacted.

Sadly what works for legitimate businesses almost always works for cybercriminals too, so there are plenty of crooks still using SMSes for phishing - an attack that's wryly known as smishing. Your phone's operating system will happily recognise when the text in an SMS looks like a URL and automatically make it clickable for you.

Mozilla is decommissioning Firefox Send and Firefox Notes, two legacy services that emerged out of the Firefox Test Pilot program. Firefox Send, the browser maker reveals, is being discontinued because it has been abused for delivering malware and phishing attacks.

Researchers at the National Institute of Standards and Technology have developed a new method called the Phish Scale that could help organizations better train their employees to avoid phishing. Many organizations have phishing training programs in which employees receive fake phishing emails generated by the employees' own organization to teach them to be vigilant and to recognize the characteristics of actual phishing emails.