Security News

Docker has fixed a vulnerability that could have allowed an attacker to gain control of a Windows system using its service. The bug, discovered by Ceri Coburn, a researcher at security consultancy Pen Test Partners, exposed Docker for Windows to privilege elevation.

Adobe just published a foursome of very tight-lipped security notifications about new patches. The bulletin APSB20-26 actually came out last week, on Patch Tuesday, leaving a gap at -25, suggesting that at least the patch in bulletin APSB20-15 was prepared in time for Patch Tuesday but didn't make the final cut, perhaps to give it time for additional testing or tweaking.

This week we discuss a customer who went to Subway for a sandwich and left with a stalker, whether there's a demon in your printer and the things you should patch now. I host the show this week with Sophos experts Mark Stockley, Paul Ducklin and Greg Iddon.

An elevation of privilege vulnerability exists when the Windows Print Spooler service improperly allows arbitrary writing to the file system. What the researchers discovered, very greatly simplified, is that with some simple PowerShell commands, any user can setup a new printer device on Windows, provided that there's already a low-level driver program installed to support the destination printer.

Among the vulnerabilities patched by Microsoft on May 2020 Patch Tuesday is CVE-2020-1048, a "Lowly" privilege escalation vulnerability in the Windows Print Spooler service. CVE-2020-1048, which affects Windows 7, 8.1, and 10 and Windows Server 2008, 2012, 2016, and 2019, arises from the Windows Print Spooler service improperly allowing arbitrary writing to the file system.
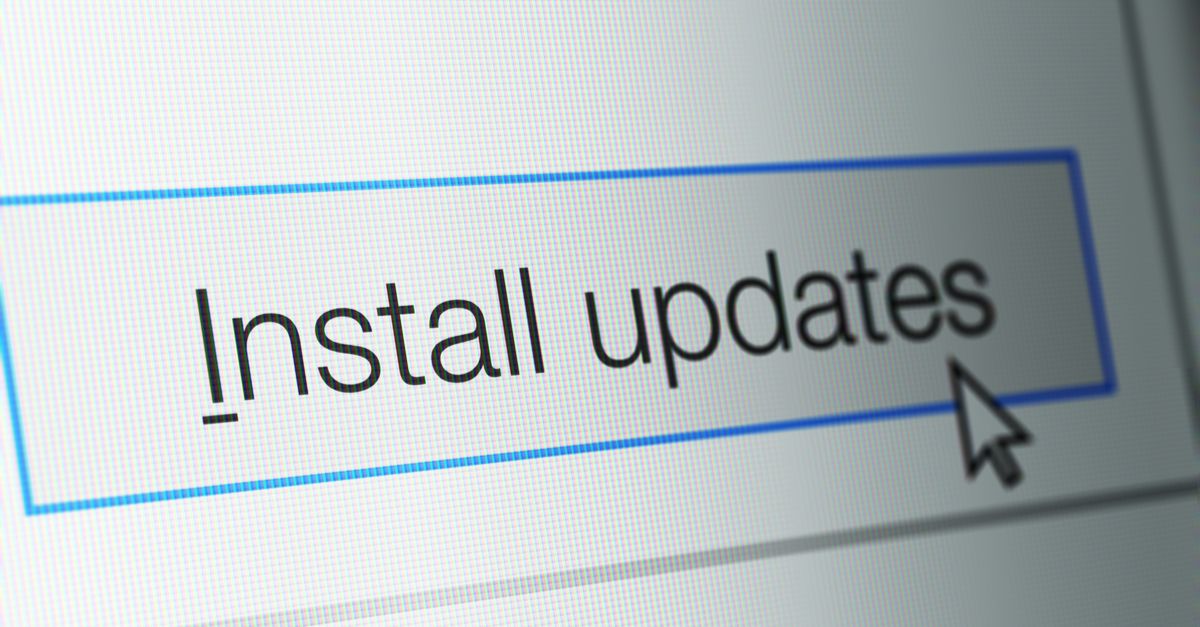
After a flurry of zero-day vulnerabilities in recent editions, May's Patch Tuesday finally gives Windows users a month off having to fix 'big' exploited or public flaws. The catch is it's still one of the biggest patch rounds Microsoft has ever released, featuring 111 CVE-level bug fixes, nearly half of which are in Windows itself.

A list posted by US-CERT this week rattles off the 10 most oft-targeted security vulnerabilities during the past three years, and finds that, shock horror, for the most part, keeping up with patching will keep you safe. Microsoft ranks highly in the list because its software is widely used, and provides the most potential targets for hackers, though on the other hand, fixes have been available for these bugs for a long while: it doesn't have to be this way, people.
Remember the Reverse RDP Attack-wherein a client system vulnerable to a path traversal vulnerability could get compromised when remotely accessing a server over Microsoft's Remote Desktop Protocol? Though Microsoft had patched the vulnerability as part of its July 2019 Patch Tuesday update, it turns out researchers were able to bypass the patch just by replacing the backward slashes in paths with forward slashes.

Microsoft's May 2020 security updates patch 111 vulnerabilities, including 16 rated critical, but none of them has been exploited in attacks or disclosed before fixes were released. "For the past three months, Microsoft has been issuing very large Patch Tuesday releases, with March fixing 115 vulnerabilities, April with 113, and now May with 111. This shows their commitment to resolving vulnerabilities in their software, and their continued engagement with the security community."

Microsoft today issued software updates to plug at least 111 security holes in Windows and Windows-based programs. May marks the third month in a row that Microsoft has pushed out fixes for more than 110 security flaws in its operating system and related software.