Security News

The heightened regulatory and legal pressure on software-producing organizations to secure their supply chains and ensure the integrity of their software should come as no surprise. In the last...

Apple has released a firmware update for AirPods that could allow a malicious actor to gain access to the headphones in an unauthorized manner. Tracked as CVE-2024-27867, the authentication issue...
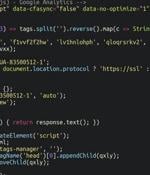
Multiple content management system (CMS) platforms like WordPress, Magento, and OpenCart have been targeted by a new credit card web skimmer called Caesar Cipher Skimmer. A web skimmer refers to...

An unknown threat actor has compromised five WordPress plugins and injected them with code that creates a new admin account, effectively allowing them complete control over WordPress installations / websites. The backdoored plugins have collectively been downloaded by 35,000+ WordPress users.
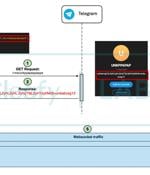
Cybersecurity researchers have discovered an updated version of an Android banking trojan called Medusa that has been used to target users in Canada, France, Italy, Spain, Turkey, the U.K., and...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Google has taken steps to block ads for e-commerce sites that use the Polyfill.io service after a Chinese company acquired the domain and modified the JavaScript library ("polyfill.js") to...

As a Cloud Security Engineer, you'll design, develop and deliver the security model of Atom bank's cloud environment ensuring that infrastructure, applications, and processes remain inline with various security standards, legal, regulatory, and industry best practice frameworks. As a Cybersecurity Architect, you will be responsible for establishing and maintaining a comprehensive information security management program to optimize the organization's cybersecurity posture to protect and enable Vertex's mission.
Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.