Security News

An open-source smart data exploration, analysis and model debugging tool for machine learning. Data scientists often need to analyze datasets both during the data preparation stage and model training, which can be overwhelming and time-consuming, especially when working on large-scale datasets.

Programmer and lawyer Matthew Butterick has sued Microsoft, GitHub, and OpenAI, alleging that GitHub's Copilot violates the terms of open-source licenses and infringes the rights of programmers. GitHub Copilot, released in June 2022, is an AI-based programming aid that uses OpenAI Codex to generate real-time source code and function recommendations in Visual Studio.

In businesses of all sizes, open-source software is a crucial component of the software supply chain, but the OSS supply chain is also facing new security issues - calling for better approaches to packaging security. In this Help Net Security video, Michael Cote, Senior Member Of Technical Staff at VMware, talks about recent VMware research, which reveals security concerns in the overall open-source software supply chain are increasing.

Open-source repository SourceHut is pulling the plug on software projects that tap into cryptocurrency and blockchain. In a post published on Monday, Oct. 31, SourceHut founder and creator Drew DeVault said he would ban projects associated with these technologies, citing their use in "Get-rich-quick" schemes and other types of scams.

As the data scientist he is, he, of course, asked the data: how good is the open source community at finding vulnerabilities in a timely manner? Finding open source vulnerabilities is typically done by the maintainers of the open source project, users, auditors, or external security researchers.

A new open-source 'S3crets Scanner' scanner allows researchers and red-teamers to search for 'secrets' mistakenly stored in publicly exposed or company's Amazon AWS S3 storage buckets. In addition to application data, source code or configuration files in the S3 buckets can also contain 'secrets,' which are authentication keys, access tokens, and API keys.

The cybersecurity industry is too happy to provide services, software, and insurance to accommodate this new normal. The market is so big and juicy that no one can get in the way of "The development of the cyber insurance market."

In this Help Net Security video, Christopher Maddalena, Director of Internal and Community Product at SpecterOps, showcases Ghostwriter, which helps you manage clients, projects, reports, and infrastructure in one application. The tool does not replace some of the more common or traditional project management tools, such as CRMs. Still, it does consolidate all relevant project information in a way for users to easily curate every aspect of their projects.
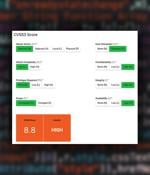
MyOpenVDP is a turnkey open-source solution allowing anyone to host their own vulnerability disclosure policy. Developed by YesWeHack, the web application is available on GitHub.

Open-source software has reached greater levels of security than ever before, but its increased adoption comes with new challenges. In this Help Net Security video, Josep Prat, Open Source Engineering Director at Aiven, illustrates how threat actors see greater use of open-source software as an opportunity, deploying new methods targeting tech professionals and open-source projects.