Security News

APTRS is an open-source reporting tool built with Python and Django. It’s made for penetration testers and security teams who want to save time on reports. Instead of writing reports by hand,...

YES3 Scanner is an open-source tool that scans and analyzes 10+ different configuration items for your S3 buckets in AWS. This includes access such as public access via ACLs and bucket policies –...

There’s been a notable shift in the types of threats targeting software developers, with a total of 17,954 open source malware packages identified in Q1 2025, according to Sonatype. Quarterly...

BlueToolkit is an open-source tool that helps find security flaws in Bluetooth Classic devices. It runs known and custom exploits to test if a device is vulnerable. Right now, it includes 43...

Exegol is a community-driven hacking environment, which helps users deploy hacking setups quickly and securely. It’s made for penetration testers, CTF players, bug bounty hunters, researchers,...

OPKSSH (OpenPubkey SSH) makes it easy to authenticate to servers over SSH using OpenID Connect (OIDC), allowing developers to ditch manually configured SSH keys in favor of identity provider-based...

This month’s roundup features exceptional open-source cybersecurity tools that are gaining attention for strengthening security across various environments. Hetty: Open-source HTTP toolkit for...

Finders Keypers is an open-source tool for analyzing the current usage of AWS KMS keys. It supports both AWS customer managed KMS keys and AWS Managed KMS keys. Use cases include: Identifying the...
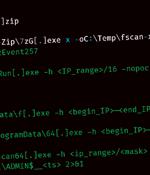
Threat hunters have uncovered a new threat actor named UAT-5918 that has been attacking critical infrastructure entities in Taiwan since at least 2023. "UAT-5918, a threat actor believed to be...

Dependency-Check is an open-source Software Composition Analysis (SCA) tool to identify publicly disclosed vulnerabilities within a project’s dependencies. The tool analyzes dependencies for...