Security News

Cybersecurity researchers have discovered a case of "forced authentication" that could be exploited to leak a Windows user's NT LAN Manager (NTLM) tokens by tricking a victim into opening a...

Now Microsoft plans to extend Kerberos in the versions of Windows and Windows Server that will ship in the next two years to help organizations move off NTLM. Here's what will change and how to prepare. How can I get ready to move off NTLM? Just over half of NTLM usage is for applications that hardcode in using NTLM. If you've done that in your own applications, you'll need to update the application: There aren't any shims or workarounds that Microsoft can do in Windows.

Microsoft has announced that it plans to eliminate NT LAN Manager (NTLM) in Windows 11 in the future, as it pivots to alternative methods for authentication and bolster security. "The focus is on...

Microsoft announced earlier this week that the NTLM authentication protocol will be killed off in Windows 11 in the future. [...]

Microsoft added a new security feature to Windows 11 that lets admins block NTLM over SMB to prevent pass-the-hash, NTLM relay, or password-cracking attacks. This will modify the legacy approach where Kerberos and NTLM authentication negotiations with destination servers would be powered by Windows SPNEGO. When connecting to a remote SMB share, Windows will try to negotiate authentication with the remote computer by performing an NTLM challenge response.

Microsoft says SMB signing will be required by default for all connections to defend against NTLM relay attacks, starting with today's Windows build rolling out to Insiders in the Canary Channel. "This changes legacy behavior, where Windows 10 and 11 required SMB signing by default only when connecting to shares named SYSVOL and NETLOGON and where Active Directory domain controllers required SMB signing when any client connected to them," Microsoft said.

The vulnerability, tracked as CVE-2023-29324, has been described as a security feature bypass. Akamai security researcher Ben Barnea, who discovered and reported the bug, noted that all Windows versions are affected, but pointed out Microsoft, Exchange.

Microsoft has confirmed it fixed a previously disclosed 'ShadowCoerce' vulnerability as part of the June 2022 updates that enabled attackers to target Windows servers in NTLM relay attacks. This NTLM relay attack method can be used by threat actors to force unpatched servers to authenticate against servers under the attacker's control, leading to a takeover of the Windows domain.
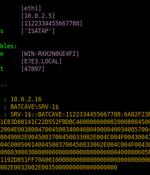
A new kind of Windows NTLM relay attack dubbed DFSCoerce has been uncovered that leverages the Distributed File System: Namespace Management Protocol to seize control of a domain. "Spooler service disabled, RPC filters installed to prevent PetitPotam and File Server VSS Agent Service not installed but you still want to relay ? Don't worry MS-DFSNM have your back," security researcher Filip Dragovic said in a tweet.

A new DFSCoerce Windows NTLM relay attack has been discovered that uses MS-DFSNM, Microsoft's Distributed File System, to completely take over a Windows domain. This service is vulnerable to NTLM relay attacks, which is when threat actors force, or coerce, a domain controller to authenticate against a malicious NTLM relay under an attacker's control.