Security News

A zero-day exploit said to have been developed by the NSA was cloned and used by Chinese government hackers on Windows systems years before the cyber-weapon was leaked online, it is claimed. Check Point put out a report on Monday digging into Chinese malware it calls Jian, and argues persuasively this particular software nasty was spawned sometime around 2014 from NSA exploit code that eventually leaked online in 2017.

New research has found evidence that a Chinese-affiliated threat group has hijacked a hacking tool previously used by the Equation Group. "Although we don't show any conclusive evidence that there is there any connection between China and the ShadowBrokers, we do show conclusive evidence that this Chinese group had in their possession a tool that was made by Equation Group, and not only that they had this tool, but they also repurposed it and used it, probably to attack many targets, including American targets," Yaniv Balmas, head of cyber research with Check Point Software, said.

Chinese state hackers cloned and started using an NSA zero-day exploit almost three years before the Shadow Brokers hacker group publicly leaked it in April 2017. "To our surprise, we found out that this APT31 exploit is in fact a reconstructed version of an Equation Group exploit called 'EpMe'," Check Point said.

A piece of malware linked by U.S. intelligence agencies to hackers believed to be backed by the Russian government remains a mystery to the private sector, which apparently hasn't found a single sample of the malware, and one researcher went as far as suggesting that it may be a false flag set up by the United States itself. In August 2020, the NSA and the FBI released a joint cybersecurity advisory detailing a piece of malware they named Drovorub.

"In 2015, Juniper revealed a security breach in which hackers modified the software the company delivered to its customers," a Wyden statement read. "Researchers subsequently discovered that Juniper had been using an NSA-designed encryption algorithm, which experts had long argued contained a backdoor, and that the hackers modified the key to this backdoor." "The American people have a right to know why NSA did not act after the Juniper hack to protect the government from the serious threat posed by supply chain hacks. A similar supply chain hack was used in the recent SolarWinds breach, in which several government agencies were compromised with malware snuck into the company's software updates," the members wrote.

Several U.S. lawmakers sent a letter to the National Security Agency last week in an effort to find out more about its role in the backdoor discovered in Juniper Networks products back in 2015, as well as the steps taken by the agency following the Juniper incident, and why those steps failed to prevent the recent SolarWinds hack. The VPN issue was related to the use of Dual Elliptic Curve Deterministic Random Bit Generator, a NIST-approved cryptographic algorithm that had been known to contain a backdoor introduced by the NSA. Juniper had made some changes to prevent abuse, but the malicious code enabled the backdoor.

As the incoming Biden administration continues to shake up federal leadership, the National Security Agency announced Friday that Rob Joyce, who is currently serving at the U.S. Embassy in London, was named to lead its cybersecurity division. Joyce will inherit the job from Anne Neuberger, who will leave the post to serve as deputy national security adviser for the National Security Council, putting her in charge of cybersecurity for the entire federal government.

The U.S. National Security Agency on Friday announced that Rob Joyce, an official who is highly respected in the cybersecurity community, has been named the agency's new director of cybersecurity. Joyce, who according to his LinkedIn profile has been working for the Defense Department for the past 32 years, replaces Anne Neuberger, who has been appointed Deputy National Security Advisor for Cyber and Emerging Technology by the upcoming Biden administration.
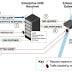
The U.S. National Security Agency on Friday said DNS over HTTPS - if configured appropriately in enterprise environments - can help prevent "Numerous" initial access, command-and-control, and exfiltration techniques used by threat actors. "DNS over Hypertext Transfer Protocol over Transport Layer Security, often referred to as DNS over HTTPS, encrypts DNS requests by using HTTPS to provide privacy, integrity, and 'last mile' source authentication with a client's DNS resolver," according to the NSA's new guidance.

The National Security Agency on Wednesday published guidance for businesses on the adoption of an encrypted domain name system protocol, specifically DNS over HTTPS. Designed to translate the domain names included in URLs into IP addresses, for an easier navigation of the Internet, DNS has become a popular attack vector, mainly because requests and responses are transmitted in plaintext. "Using DoH with external resolvers can be good for home or mobile users and networks that do not use DNS security controls. For enterprise networks NSA recommends using only designated enterprise DNS resolvers in order to properly leverage essential enterprise cybersecurity defenses, facilitate access to local network resources, and protect internal network information," the NSA notes.