Security News

Taiwanese hardware vendor QNAP has added a Security Center with ransomware protection capabilities to the latest version of its QTS operating system for network-attached storage (NAS) devices. [...]

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Zyxel has released patches for three critical vulnerabilities affecting two network-attached storage devices that have recently reached end-of-vulnerability-support. The vulnerabilities have been discovered and reported by Timothy Hjort, a vulnerability researcher with Outpost24's Ghost Labs.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Zyxel has released security updates to address critical flaws impacting two of its network-attached storage (NAS) devices that have currently reached end-of-life (EoL) status. Successful...

Zyxel Networks has released an emergency security update to address three critical vulnerabilities impacting older NAS devices that have reached end-of-life. Although both NAS models reached the end of their support period on December 31, 2023, Zyxel released fixes for the three critical flaws in versions 5.21(AAZF.17)C0 for NAS326 and 5.21(ABAG.14)C0 for NAS542.
Taiwanese company QNAP has rolled out fixes for a set of medium-severity flaws impacting QTS and QuTS hero, some of which could be exploited to achieve code execution on its network-attached...

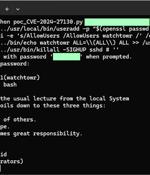
Researchers have found 15 vulnerabilities in QNAP's network attached storage devices, and have released a proof-of-concept for one: an unauthenticated stack overflow vulnerability that may be leveraged for remote code execution. "Given the shared-access model of the NAS device, which permits sharing files with specific users, both authenticated and unauthenticated bugs were of interest to us," they said.

Threat actors are actively scanning and exploiting a pair of security flaws that are said to affect as many as 92,000 internet-exposed D-Link network-attached storage (NAS) devices. Tracked...

Attackers are now actively targeting over 92,000 end-of-life D-Link Network Attached Storage devices exposed online and unpatched against a critical remote code execution zero-day flaw. Mirai variants are usually designed to add infected devices to a botnet that can be used in large-scale distributed denial-of-service attacks.