Security News

Cybersecurity researchers have discovered a new variant of the Gafgyt botnet that's targeting machines with weak SSH passwords to ultimately mine cryptocurrency on compromised instances using their GPU computational power. The infected devices are corralled into a botnet capable of launching distributed denial-of-service attacks against targets of interest.

Australian gold mining firm Evolution Mining has announced on Monday that it became aware on 8 August 2024 of a ransomware attack impacting its IT systems, and has been working with its external cyber forensic experts to investigate the incident. "Based on work to date, the Company believes the incident is now contained," Evolution Mining said.

Evolution Mining has informed that it has been targeted by a ransomware attack on August 8, 2024, which impacted its IT systems. [...]

Threat actors are exploiting a misconfiguration in Selenium Grid, a popular web app testing framework, to deploy a modified XMRig tool for mining Monero cryptocurrency. Selenium Grid is open-source and enables developers to automate testing across multiple machines and browsers.
Cybersecurity researchers are sounding the alarm over an ongoing campaign that's leveraging internet-exposed Selenium Grid services for illicit cryptocurrency mining. Selenium Grid, part of the Selenium automated testing framework, enables parallel execution of tests across multiple workloads, different browsers, and various browser versions.
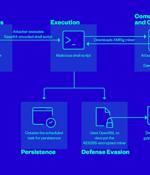
Cybersecurity researchers have found that it's possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining. Jenkins, a popular continuous integration and continuous delivery platform, features a Groovy script console that allows users to run arbitrary Groovy scripts within the Jenkins controller runtime.

Security researchers have shed more light on the cryptocurrency mining operation conducted by the 8220 Gang by exploiting known security flaws in the Oracle WebLogic Server. "The threat actor...

Cybersecurity researchers have uncovered a new malware campaign that targets publicly exposed Docket API endpoints with the aim of delivering cryptocurrency miners and other payloads. Included...

Northern Minerals issued an announcement earlier today warning that it suffered a cybersecurity breach resulting in some of its stolen data being published on the dark web. The firm is publicly traded on the Australian Securities Exchange under the ticker 'NTU,' so it is legally obliged to disclose any data breach incidents promptly.

The threat actors behind the RedTail cryptocurrency mining malware have added a recently disclosed security flaw impacting Palo Alto Networks firewalls to its exploit arsenal. The addition of the...