Security News

The FBI has cut off a network of Kremlin-controlled computers used to spread the Snake malware which, according to the Feds, has been used by Russia's FSB to steal sensitive documents from NATO members for almost two decades. After identifying and stealing sensitive files on victims' devices, Turla exfiltrated them through a covert network of unwitting Snake-compromised computers in the US. In effect, Snake can infect Windows, Linux, and macOS systems, and use those network nodes to pass data stolen from victims along to the software nasty's Russian spymasters.

An Australian military helicopter crash was reportedly caused by failure to apply a software patch, with a heft side serving of pilot error. The helicopter in question is an MRH-90 Taipan operated by the Australian Army and was engaged in what's been described as "a routine counter-terrorism training activity" on March 23rd when it ditched just off a beach in the State of New South Wales.

An Estonian national has been charged in the U.S. for purchasing U.S.-made electronics on behalf of the Russian government and military. Court documents allege that Shevlyakov operated front companies that were used to import sensitive electronics from U.S. manufacturers.

Government and military organizations in the Asia Pacific region are being targeted by a previously unknown advanced persistent threat actor, per the latest research. Singapore-headquartered Group-IB, in a report shared with The Hacker News, said it's tracking the ongoing campaign under the name Dark Pink and attributed seven successful attacks to the adversarial collective between June and December 2022.

Attacks targeting government agencies and military bodies in multiple countries in the APAC region have been attributed to what appears to be a new advanced threat actor that leverages custom malware to steal confidential information. Security researchers refer to this group as Dark Pink or Saaiwc Group, noting that it employs uncommon tactics, techniques, and procedures.

The Computer Emergency Response Team of Ukraine this week disclosed that users of the Delta situational awareness program received phishing emails from a compromised email account belonging to the Ministry of Defense. The attacks, which have been attributed to a threat cluster dubbed UAC-0142, aimed to infect systems with two pieces of data-stealing malware referred to as FateGrab and StealDeal.

A compromised Ukrainian Ministry of Defense email account was found sending phishing emails and instant messages to users of the 'DELTA' situational awareness program to infect systems with information-stealing malware. The campaign was highlighted in a report today by CERT-UA, which warned Ukrainian military personnel of the malware attack.

The US Department of Justice unsealed a 16-count indictment today accusing five Russians, an American citizen, and a lawful permanent US resident of smuggling export-controlled electronics and military ammunition out of the United States for the Russian government. Alexey Brayman, the lawful permanent US resident; and Vadim Yermolenko, the US citizen, were both apprehended in the United States.
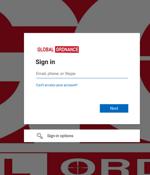
A state-sponsored hacking group with links to Russia has been linked to attack infrastructure that spoofs the Microsoft login page of Global Ordnance, a legitimate U.S.-based military weapons and hardware supplier. The cybersecurity firm said it discovered 38 domains, nine of which contained references to companies like UMO Poland, Sangrail LTD, DTGruelle, Blue Sky Network, the Commission for International Justice and Accountability, and the Russian Ministry of Internal Affairs.

Defense contractors hold information that's vital to national security and will soon be required to meet Cybersecurity Maturity Model Certification compliance to keep those secrets safe. Nation-state hackers are actively and specifically targeting these contractors with sophisticated cyberattack campaigns.