Security News

Microsoft has shared a workaround for users affected by a known issue that blocks Windows security updates from deploying on some Windows 11 24H2 systems. [...]

Windows 11's January 28 optional update has fixed a long-standing issue in Windows 11 24H2 that prevents non-admin users from changing their time zone in Date & Time Settings. [...]

Microsoft Edge 133 is now rolling out globally, and it ships with several improvements, including a new scareware blocker feature. In addition, Microsoft is updating the backend of the Downloads...
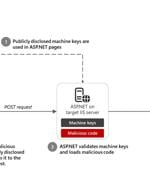
Microsoft is warning of an insecure practice wherein software developers are incorporating publicly disclosed ASP.NET machine keys from publicly accessible resources, thereby putting their...

Microsoft warns that attackers are deploying malware in ViewState code injection attacks using static ASP. NET machine keys found online. [...]

CISA warned U.S. federal agencies on Thursday to secure their systems against ongoing attacks targeting a critical Microsoft Outlook remote code execution (RCE) vulnerability. [...]

Microsoft has released a PowerShell script to help Windows users and admins update bootable media so it utilizes the new "Windows UEFI CA 2023" certificate before the mitigations of the BlackLotus...

Microsoft has released a PowerShell script to help Windows users and admins update bootable media so it utilizes the new "Windows UEFI CA 2023" certificate before the mitigations of the BlackLotus...

A help desk phishing campaign targets an organization's Microsoft Active Directory Federation Services (ADFS) using spoofed login pages to steal credentials and bypass multi-factor authentication...

The US Cybersecurity & Infrastructure Security Agency (CISA) has added four vulnerabilities to its Known Exploited Vulnerabilities catalog, urging federal agencies and large organizations to apply...